
Using Cloudsmith as a Dependency Firewall

Organizations rely heavily on open source packages from public repositories like Maven Central, npm, PyPI, RubyGems, Docker Hub, and many more. While these repositories are vital for development, they also present risks as they are targets for malicious actors exploiting vulnerabilities within the software supply chain.
Many software development teams connect their IDEs and their build tools directly to these public repositories, downloading open source software (OSS) packages without any controls or checks. This can expose your production system to security vulnerabilities and compliance issues.
Cloudsmith’s cloud-native artifact management platform is ideally positioned to help you manage and control your open source dependencies. By using Cloudsmith as a dependency firewall, you create a layer of protection between your systems and these threats. A key set of Cloudsmith features, including package management, package scanning, upstreams, and policy management, ensures all binaries and dependencies are verified and controlled so you can increase your level of security and compliance.
Challenges Your Organization Faces
Let's explore common hurdles organizations face when managing open source software and proprietary binaries, and how a dependency firewall can mitigate these risks.
Lack of Visibility Over Dependencies
It can be difficult to determine what open source dependencies, including transitive dependencies, are in your software builds.
Uncontrolled Package Consumption
Developers may pull packages directly from public repositories, potentially introducing vulnerabilities.
Reliability of Public Repositories
Public repositories don’t provide any guarantees that a package that was there yesterday, and that you now depend on, will still be there today. The repositories themselves also don’t offer SLAs and may suffer downtime.
License Compliance Risks
Open source software can contain a dizzying variety of licenses. Inadvertently introducing new types of OSS licensing can create a threat to legal compliance and alter the legal status of your software, exposing you to litigation.
Cloudsmith's Dependency Firewall
Cloudsmith's Dependency Firewall is a set of features built to secure and control your software binaries and their dependencies. Here’s how to use it to empower your team.
Single Source of Truth
Centralize all software assets in Cloudsmith for a comprehensive view of all packages, across all formats. Cloudsmith offers native support for over 30 package types, including raw digital assets, so all of these artifacts are subject to the same controls.
Upstream Proxying and Caching
Instead of allowing developers to download OSS directly from public repositories, set up upstreams to proxy and cache OSS artifacts from public sources through Cloudsmith. Upstreams ensure all dependencies are under your control, safeguarding against outages or unexpected removals of OSS packages from public repositories.
Malware and Vulnerability Scanning
Automatically scan all packages for vulnerabilities and malware upon upload to Cloudsmith, when they’re fetched from upstream sources.
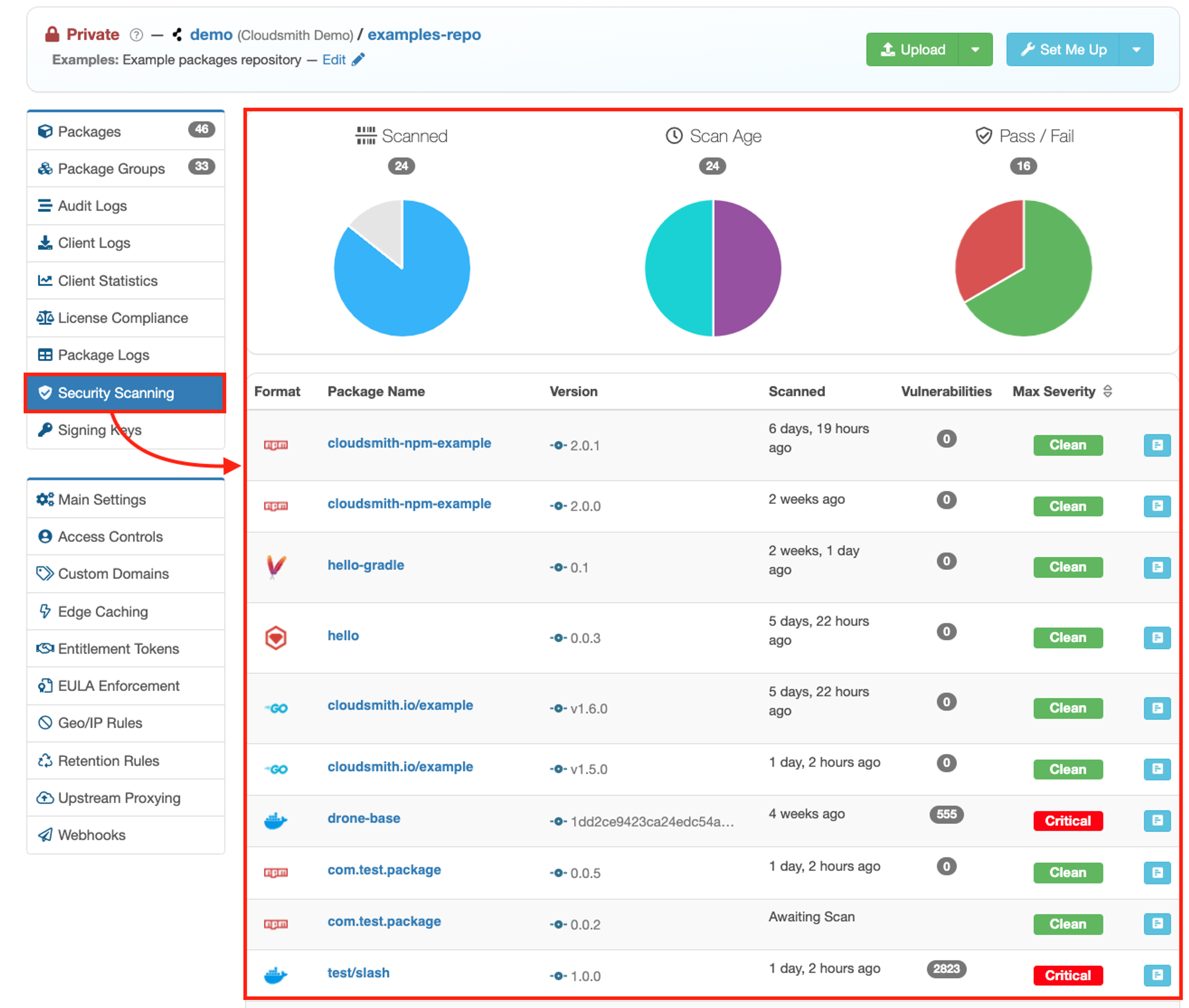
Cloudsmith also allows you to rescan packages, so you can be protected against vulnerabilities that may be discovered in a package after it’s already been cached by Cloudsmith.
License Scanning
Automatically parse package metadata for license info and match it against the SPDX License list. You’ll be able to see all OSS licenses you’ve introduced by way of dependencies.
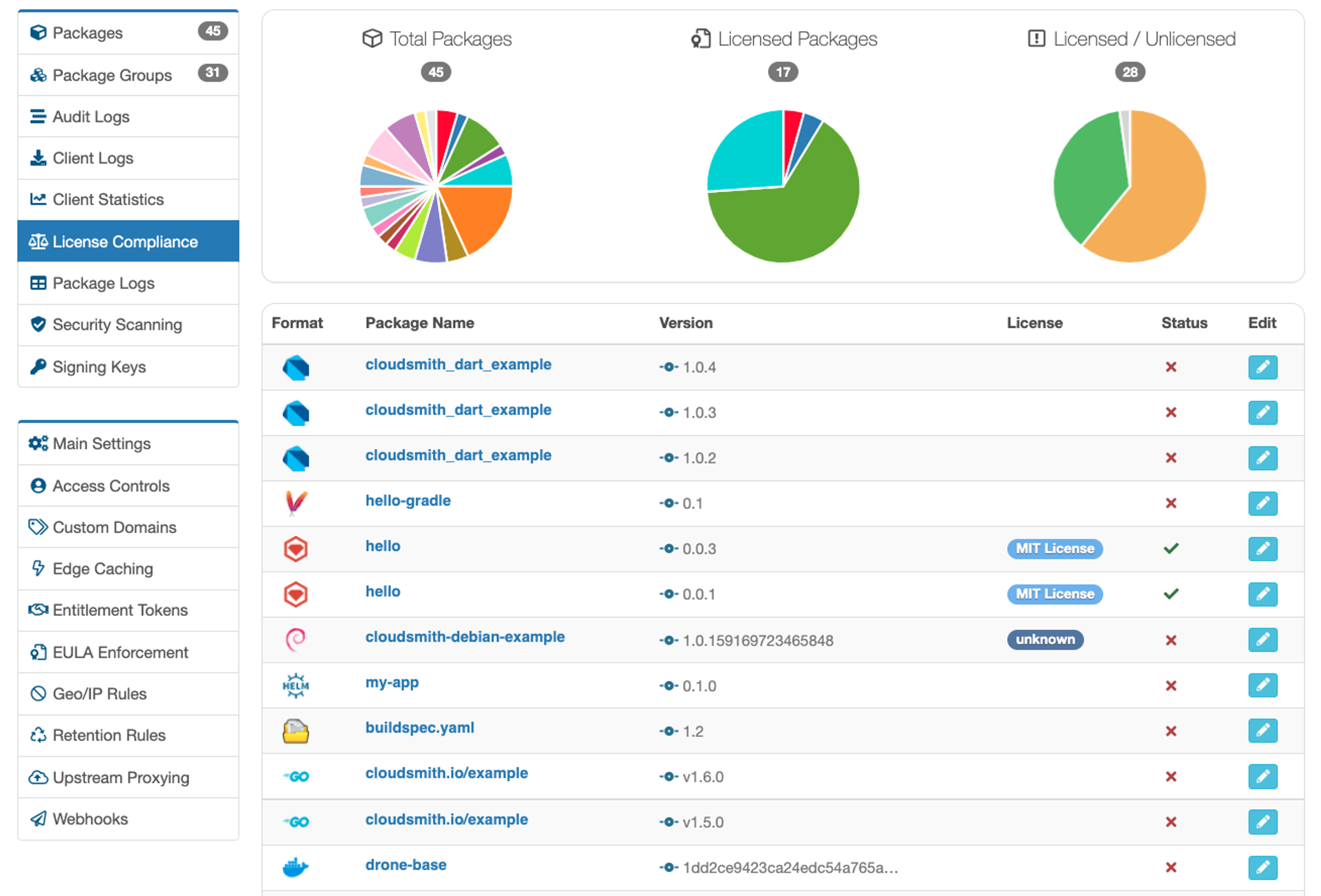
Policy Management
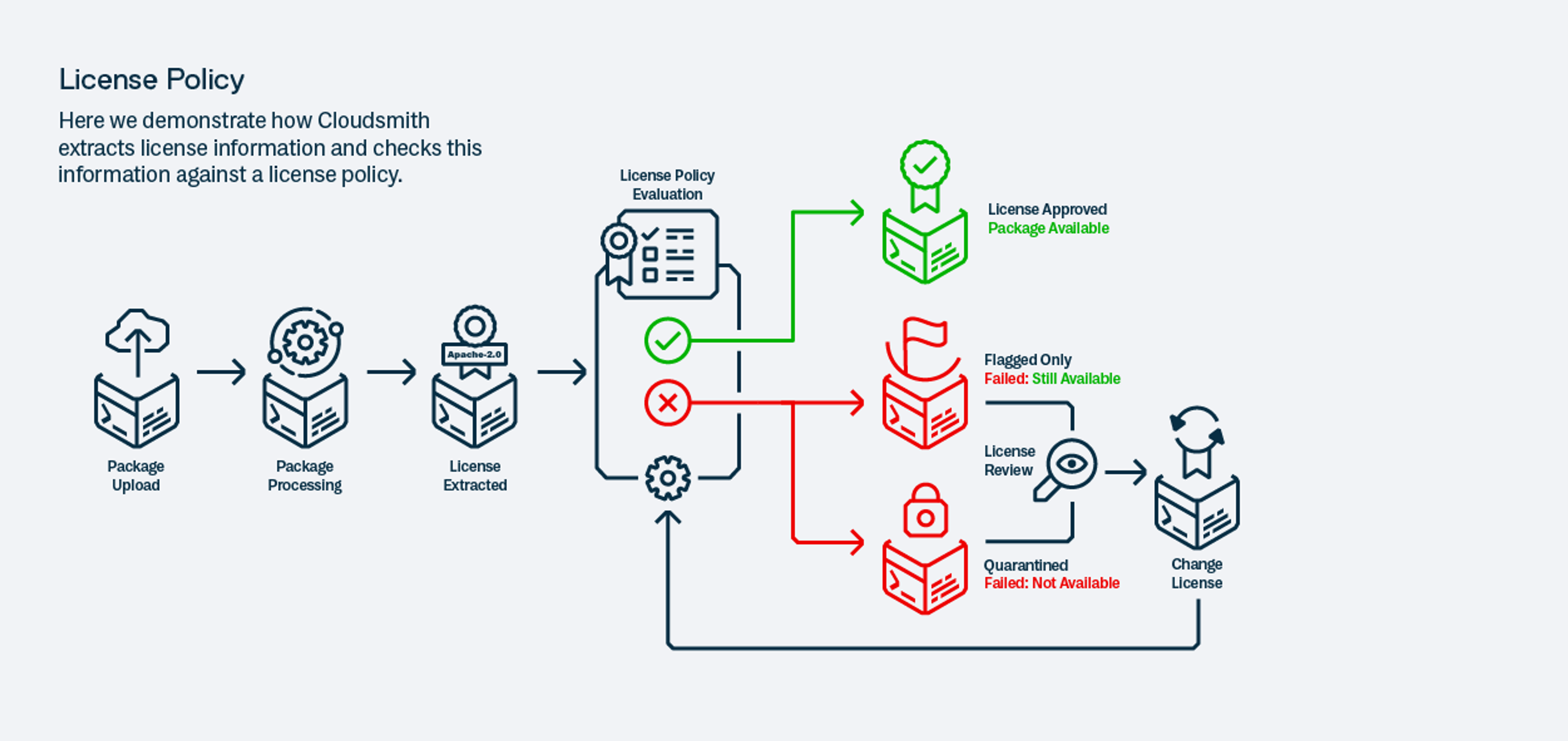
The key to making use of data produced by vulnerability, malware, and license scanning to actually protect your software supply chain is Cloudsmith’s policy management system. Creating polices allows you to implement sophisticated rules that govern whether packages will be allowed to enter builds, or will be subject to quarantine. Policy types include:
Quarantine: Cloudsmith can enforce quarantine measures for packages that fail policy checks. This can be configured to prevent quarantined packages from being used until they are reviewed by a security team, and ultimately approved or permanently blocked.
Fine-Grained Rules: Cloudsmith’s policy engine uses the same powerful boolean logic as our package search engine. This lets you create detailed rules that consider various package attributes, such as version numbers or metadata, ensuring highly targeted and effective policy enforcement.
Deny Policies: Your security team may maintain a list of OSS packages that they’ve determined should not be used by your organization, for whatever reason. Create deny lists that prevent the downloading or use of specific packages known to pose security risks or that do not meet your compliance standards.
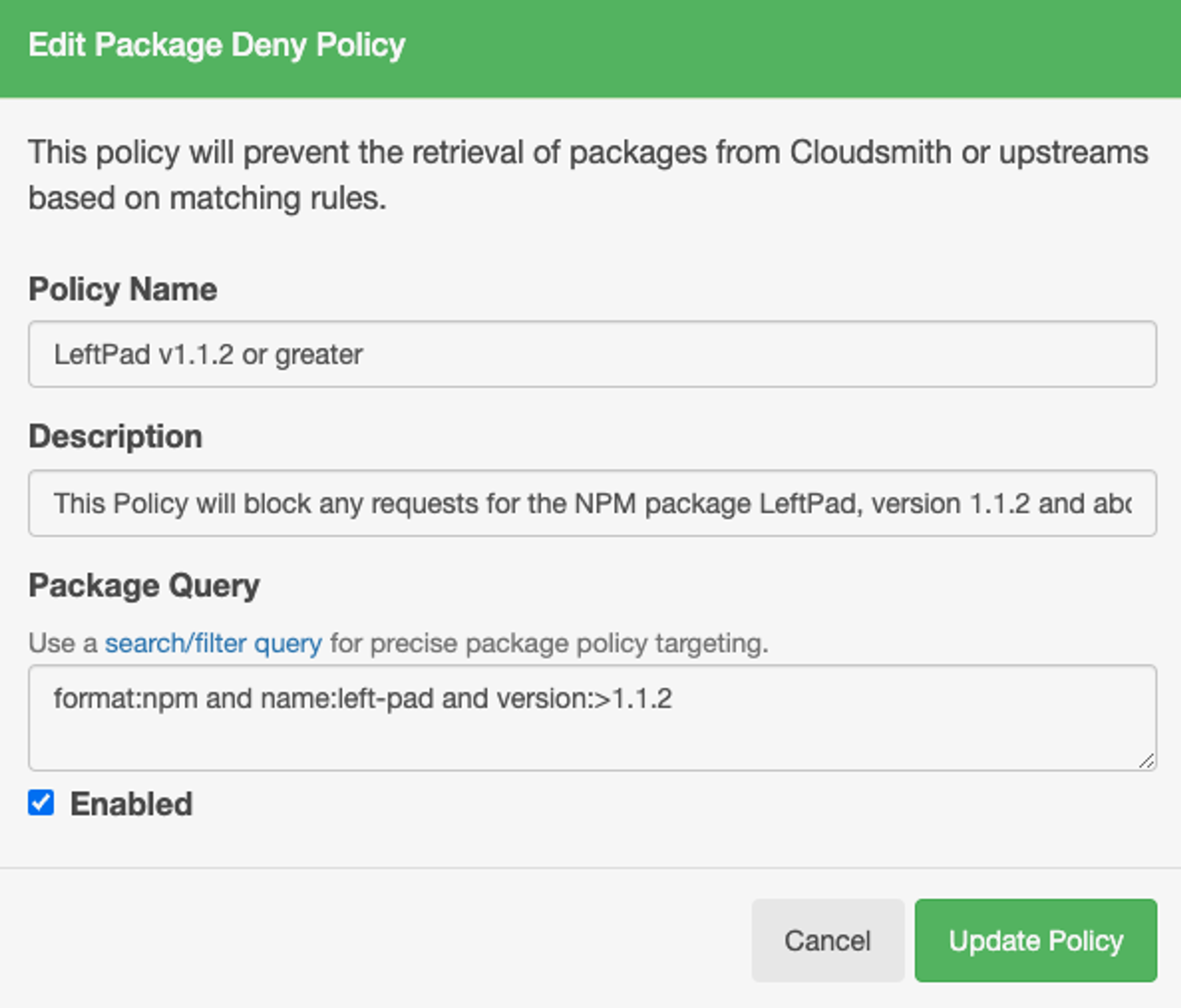
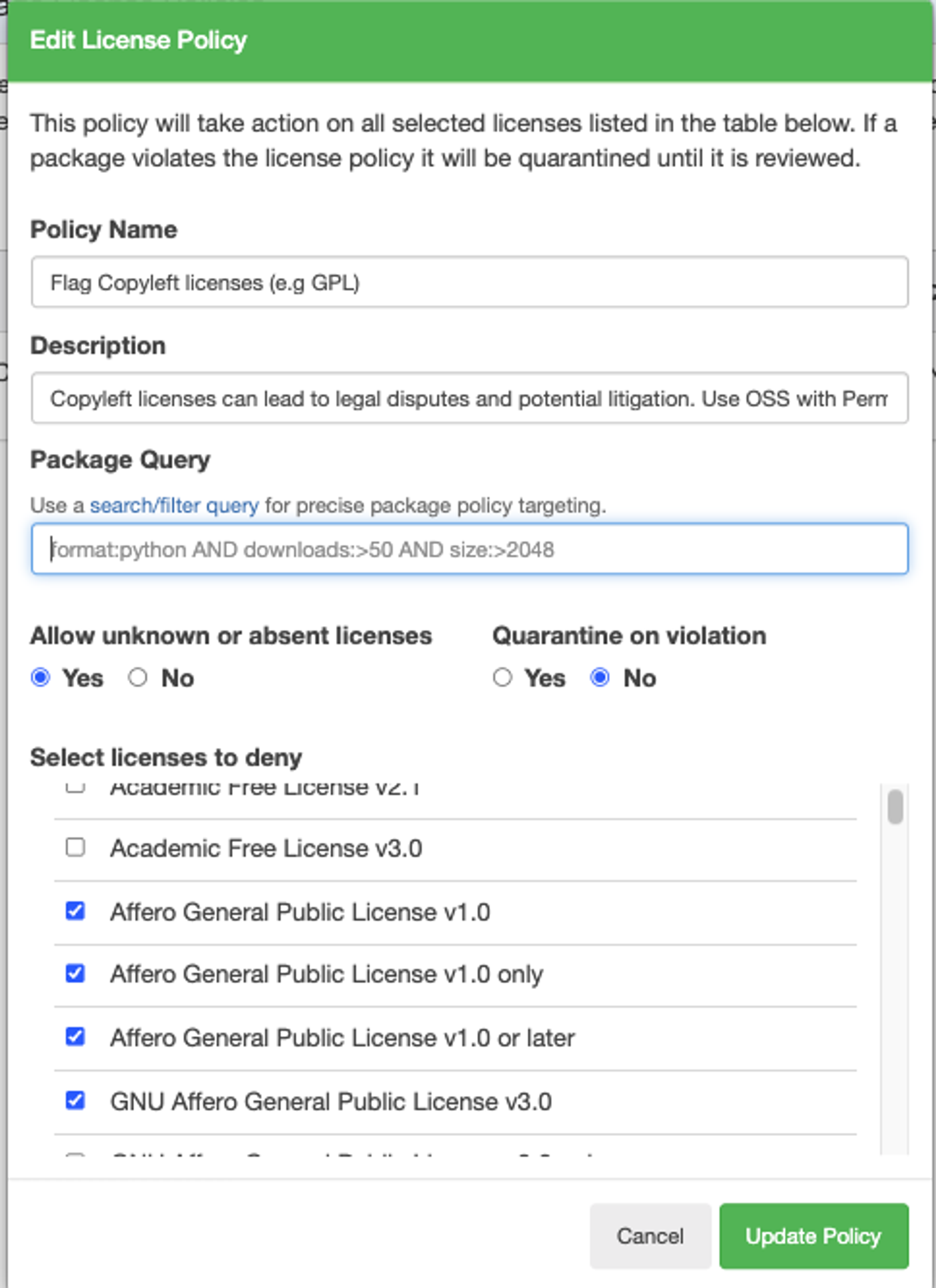
License Policies: Enforce compliance with corporate licensing standards by flagging or quarantining packages that use restricted licenses such as copyleft GPL. This helps avoid legal risks associated with non-compliance.
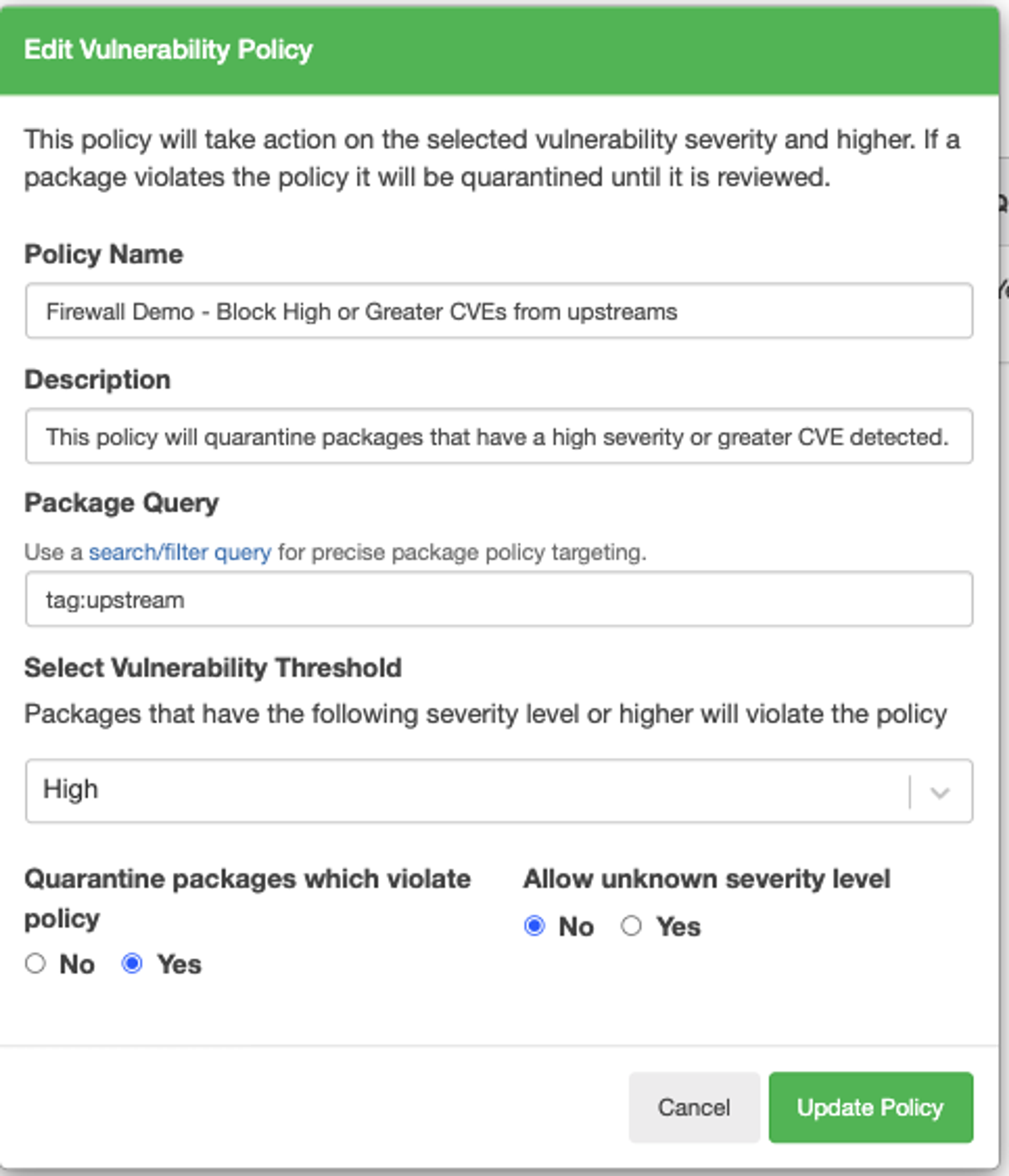
Vulnerability Policies: Automatically flag, and optionally quarantine, packages based on the severity of detected vulnerabilities. For instance, you might set a policy to block any package that has high-severity CVEs. You might also want to notify build teams when medium-severity CVEs are detected.
Automating Dependency Management
One of Cloudsmith’s core values is “automate everything.” By leveraging webhooks, comprehensive APIs, and integration with Terraform, you can automate package management to enforce security policies more efficiently. Key automation features include:
- APIs: Programmatically manage artifacts, create and enforce policies, query metadata and initiate scans, allowing for deep integration into your software development lifecycle.
- Webhooks: Automate actions within your CI/CD pipelines or integrate with ChatOps solutions (like Slack alerts) to keep your team informed about package events in real time.
- Terraform Provider: Manage Cloudsmith resources using Infrastructure as Code (IaC), ensuring that your artifact management practices are as robust and reproducible as the rest of your infrastructure.
These automation tools help enforce your Dependency Firewall by ensuring consistent policy application and facilitating proactive responses to security or compliance issues.
Zero Trust Security
A vital component of creating a dependency firewall is securing the identities of developers.
By configuring default privileges, enforcing MFA, utilizing Security Assertion Markup Language SAML, and provisioning identities using System for Cross-domain Identity Management SCIM, Cloudsmith ensures that only authenticated users can access and manage software packages. Additionally, with OpenID Connect OIDC, Cloudsmith supports short-lived access tokens instead of long-lived API keys, significantly reducing the risk of credential theft.
This robust identity management framework prevents unauthorized access and forms a critical barrier in your software supply chain, protecting your assets from potential breaches.
Use Cases for Cloudsmith’s Dependency Firewall
Get Visibility Over Dependencies
View all your binaries and dependencies in one central location to easily manage and audit your software assets.
View all the dependencies sourced from a public repository by searching for tag:upstream.
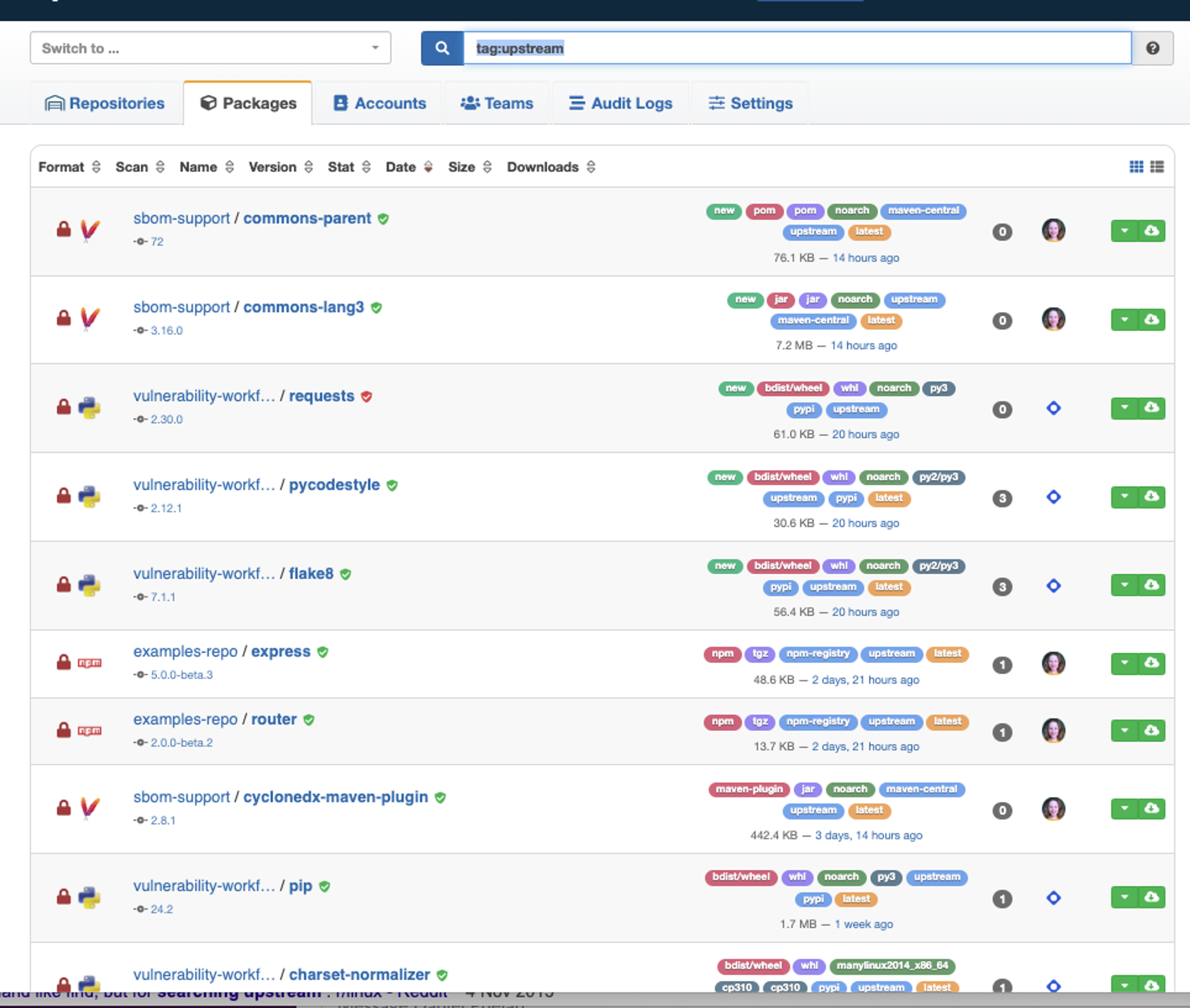
Find out if your organization depends on vulnerable packages right from our search.
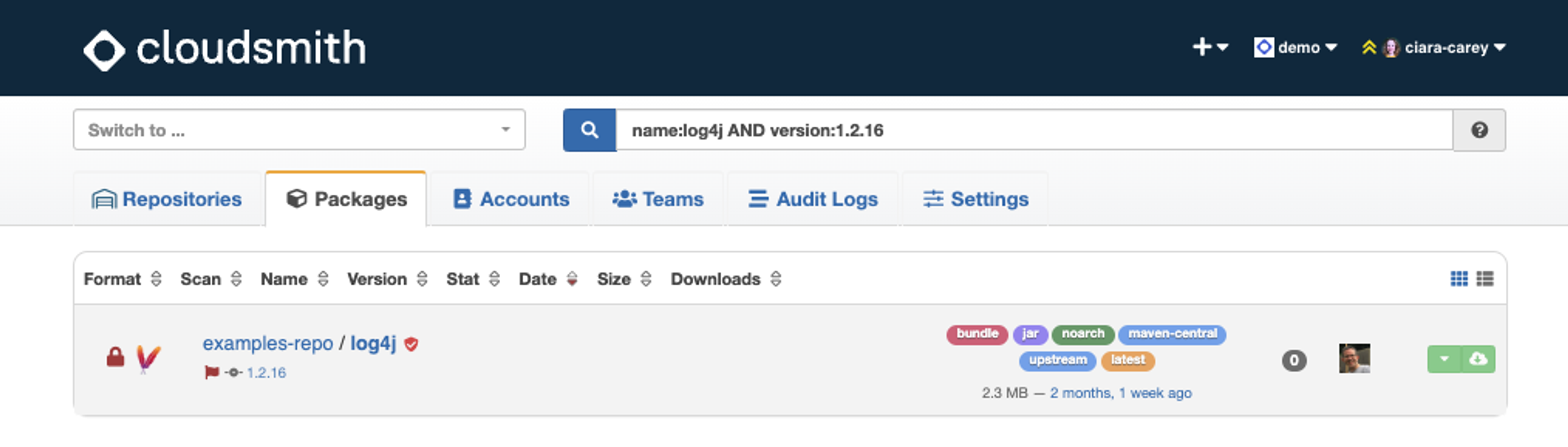
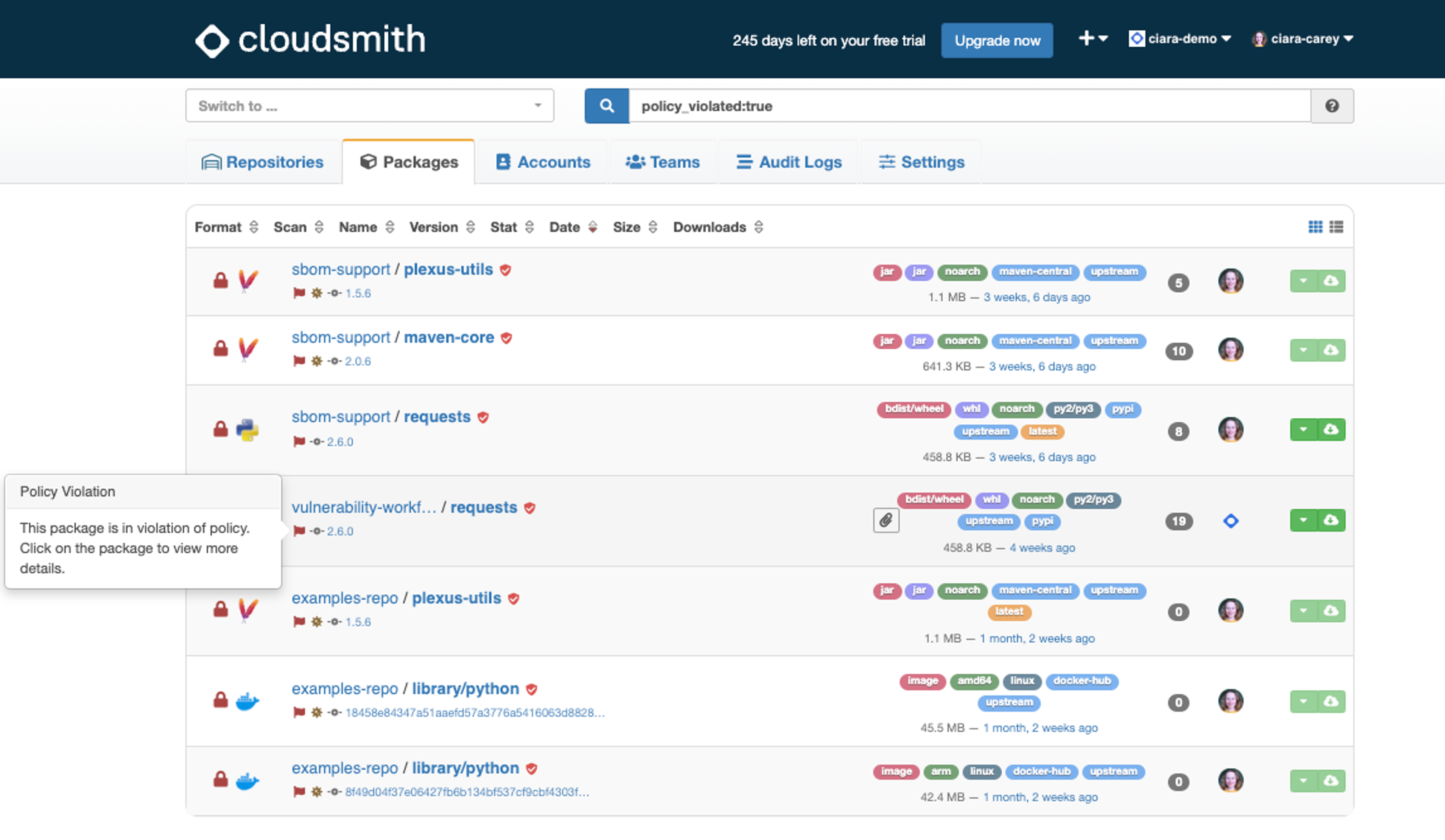
Find all the packages in your organization that violate a policy by searching for policy_violated:true.
Control Package Consumption
Use Cloudsmith’s upstreams and policy manager to set up rules and checks on packages that developers pull in. This way, you’re implementing protections before packages hit your build tools.
Protect Against Unreliability External Repositories
Create upstreams against public repositories so all your dependencies are cached in Cloudsmith, safeguarding against availability issues and unexpected removals.
License Compliance Risks
Automatically enforce policies to block or notify about dependencies that use copyleft-style licenses, ensuring compliance and avoiding potential legal disputes.
To safeguard your organization's software supply chain against emerging threats, Cloudsmith provides an essential layer of security with its Dependency Firewall. By integrating package scanning, policy management, and upstream proxying, Cloudsmith ensures that your dependencies are not only secure but fully compliant.
Ready to enhance your security and compliance measures? Start a free trial with Cloudsmith or contact our sales team for a personalized consultation to see how our solutions can meet your specific needs.
More articles


Securing LLM dependencies against serialisation attacks

Top 10 most popular LLM models on Hugging Face

Protect your software supply chain from typosquatting with Cloudsmith

Securing AI-generated code with Cloudsmith

