
Target, Track and Trace your Vulnerabilities

Lock your sights on the black box hiding untold vulnerabilities in your repository and shine a light inside to find out what monster's lurk within. Yes, I'm talking about running on-demand security scans against supported packages within your repository. If you are a velocity or ultra customer, you can start making use of security scanning today!
Not only can you run security scans, but you can track which packages are vulnerable across your repository, alongside trace when vulnerabilities were introduced by looking up the vulnerability scan results for a specific package version via our API.
With Cloudsmith's security scanning, you can uncover packages that have become vulnerable over time. The version's that introduced insecurities are visible within our repository view and our new security scanning insights view, leaving those pesky vulnerabilities nowhere left to hide!
On-Demand Security Scanning
All newly uploaded packages and images get scanned for vulnerabilities as soon as they reach Cloudsmith; however, if for any reason you wish to rerun a security scan, you can do so at any time. Don't worry; we still keep all historic security scan results to track and trace when vulnerabilities get discovered, and they are always accessible via our API should you need them.
You can run security scans daily, weekly, monthly, or using the best cadence for you and your organization. Our daily updated vulnerabilities database is updated 365 days a year, allowing you to scan every image up to a maximum of once a day, every day, to combat emerging threats.
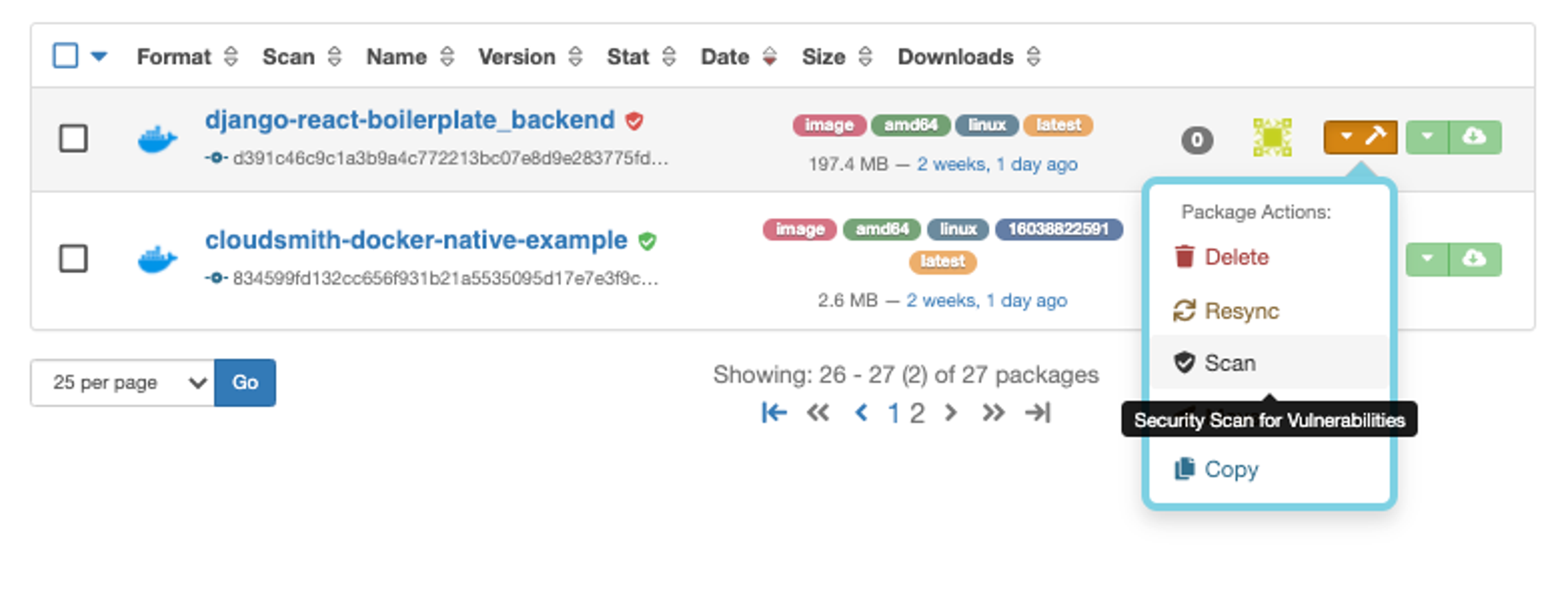
To make this easy, you can scheduled multiple images for security scanning and we will process these for you until everything has been rescanned.
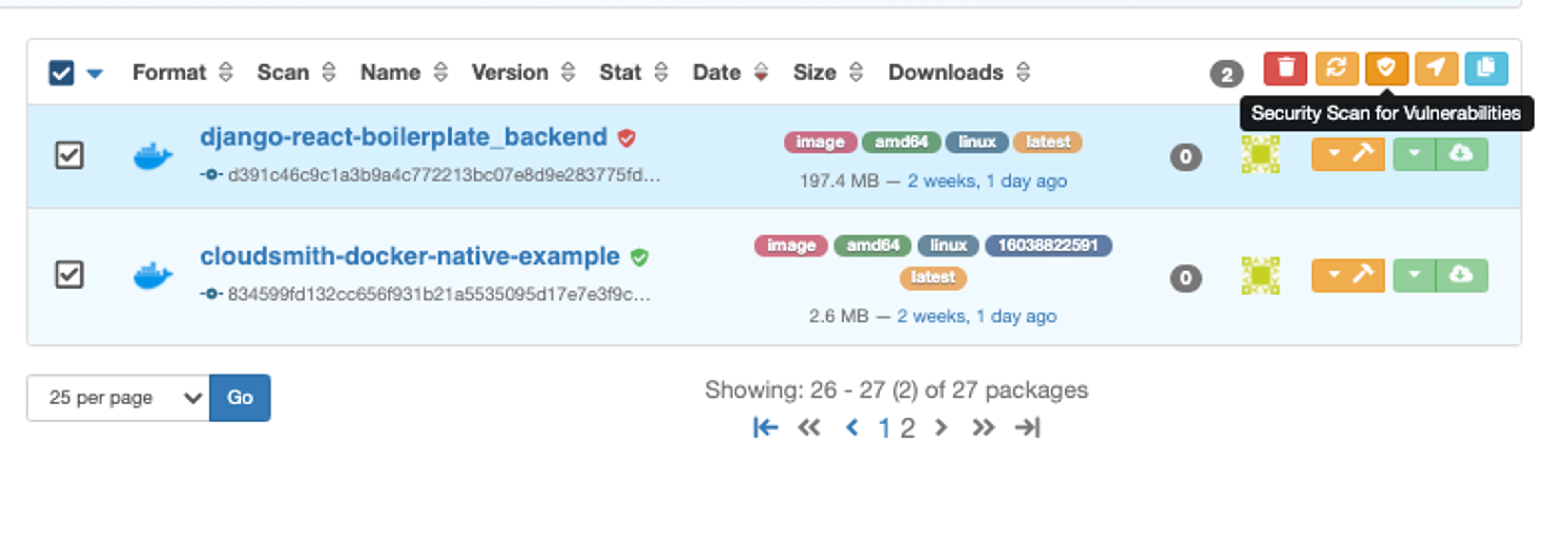
Security Scanning UI
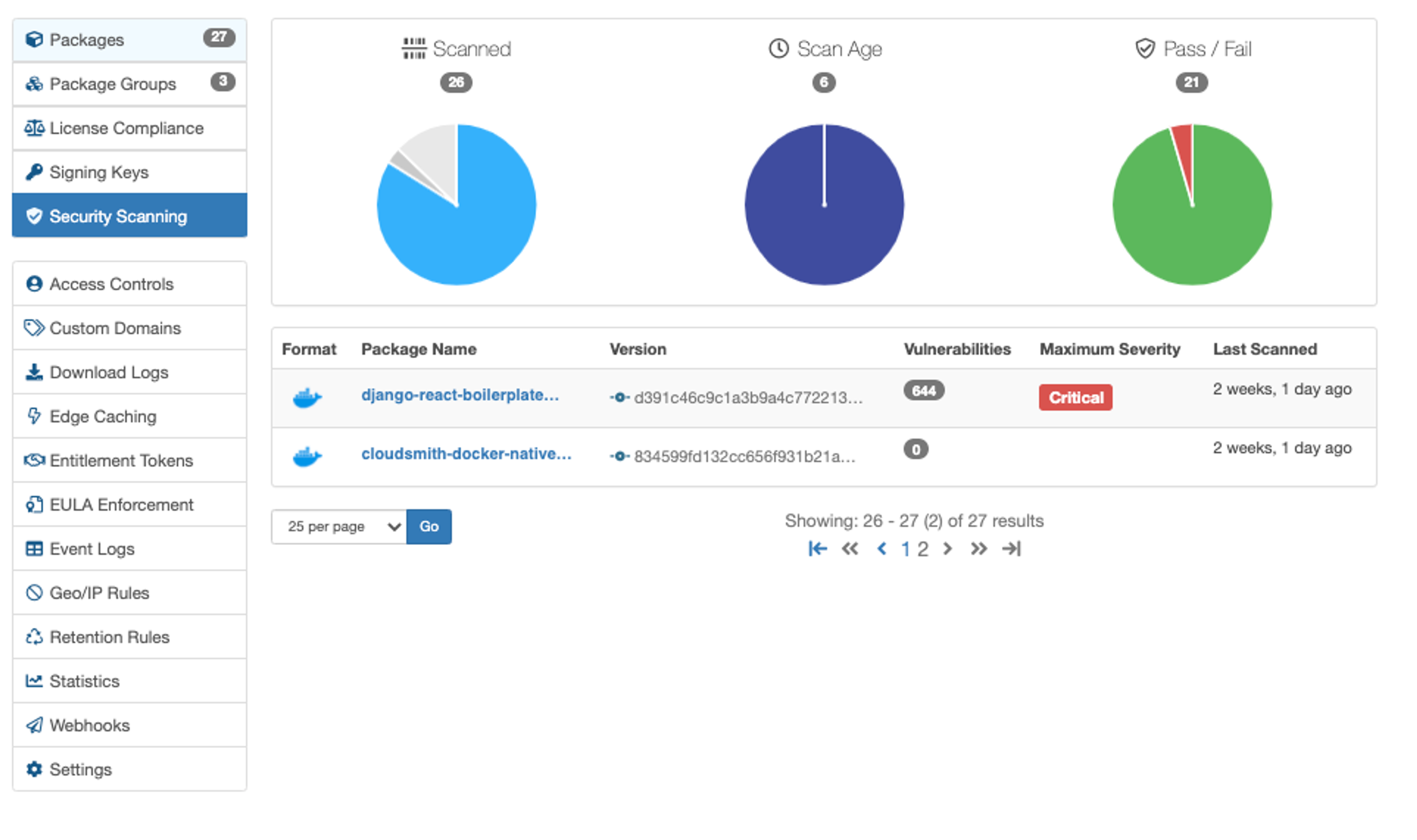
You can find a summary report of your repository's health in the Security Scanning view for all supported security scanning formats. From this view, you can view your security scanning queue, check your security scans' age, and even compare pass and fail rates across an entire repository.
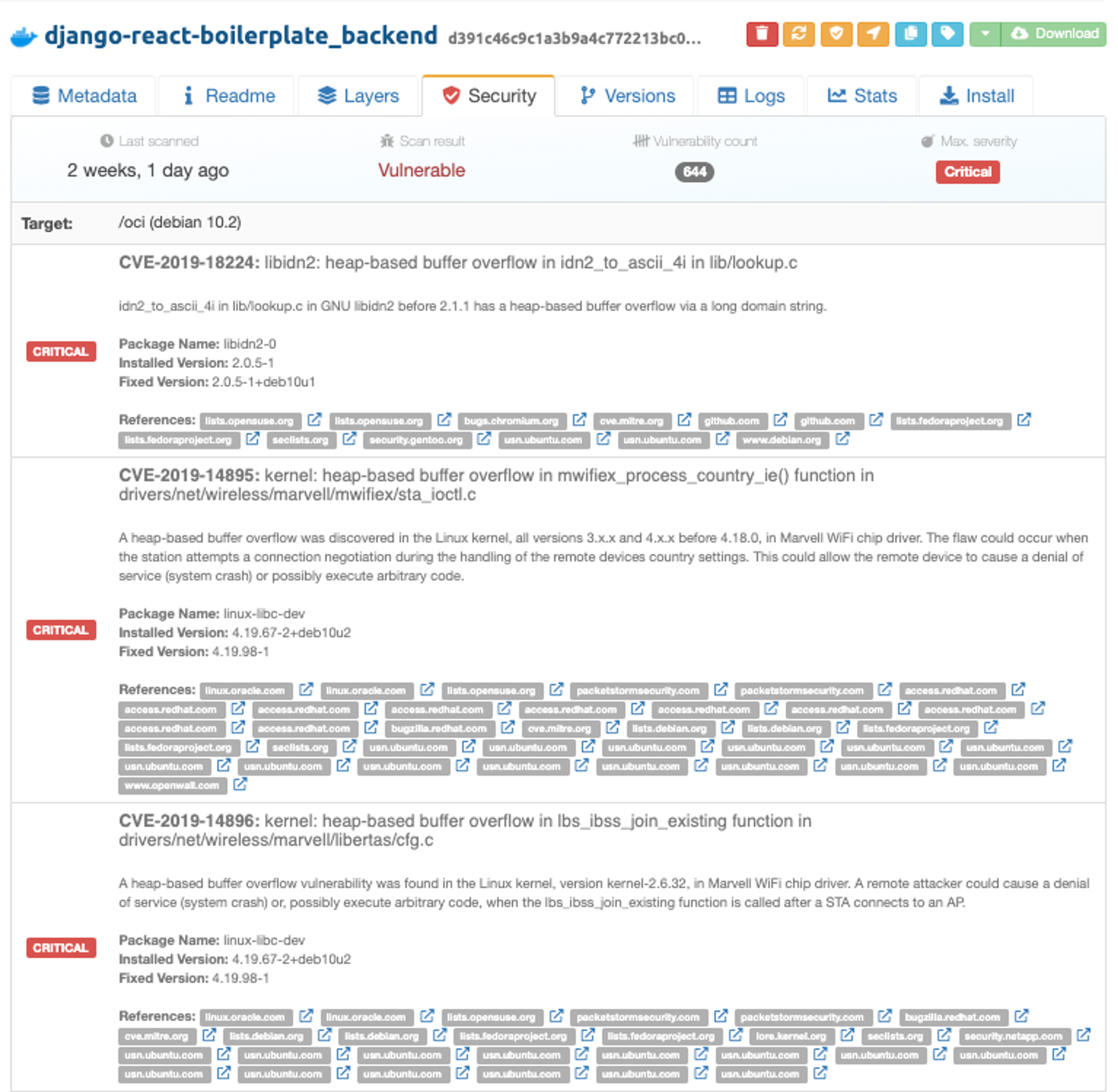
If you need more information on a specific vulnerability, you can click on the package name and the vulnerability scan results will be displayed in full for your latest security scan:
Using our Vulnerability API
Finally, we offer programatic access for scan results and historic scan results via our Vulnerability API. You can discover find vulnerabilities within your namespace, repository, and package, and drill down deeper into the exact CVE's by looking up the sequential scan_id.
For example, this is an a request to what would return the first scan for a package within an organisation/repository using the package identifier.
curl --request GET \
--url https://api.cloudsmith.io/vulnerabilities/ORGANISATION/REPOSITORY/PACKAGE_IDENTIFIER/SCAN_ID \
--header 'X-Api-Key: API-KEY'In this case, the image has no known vulnerabilities and the structure of the response looks like the following:
{
"identifier":"uurD7vaPNmOzPXtf",
"created_at":"2020-11-13T00:04:21.371641Z",
"package":{
"identifier":"Ce341YZ60Qz4",
"name":"secure-docker-native-example",
"version":"fb5489d067026892d5518110bdbe504f8ebe7e4743baae19914485fb7ed67294",
"url":"https://api.cloudsmith.io/packages/ORGANISATION/REPO/PACKAGE_IDENIFIER/"
},
"scan_id":1,
"has_vulnerabilities":false,
"num_vulnerabilities":0,
"max_severity":"Unknown",
"scan":{
"target":"/oci (alpine 3.9.6)",
"type":"alpine",
"results":[
]
}
}However if the image was vulnerable, it may look a little similar to the following:
{
"identifier":"uurD7vaPNmOzPXtf",
"created_at":"2020-11-13T00:04:21.371641Z",
"package":{
"identifier":"Ce341YZ60Qz4",
"name":"secure-docker-native-example",
"version":"fb5489d067026892d5518110bdbe504f8ebe7e4743baae19914485fb7ed67294",
"url":"https://api.cloudsmith.io/packages/ORGANISATION/REPO/PACKAGE_IDENIFIER/"
},
"scan_id":1,
"has_vulnerabilities":false,
"num_vulnerabilities":0,
"max_severity":"Unknown",
"scan":{
"target":"/oci (alpine 3.9.6)",
"type":"alpine",
"results":[
{
"vulnerability_id":"CVE-2019-9705",
"package_name":"cron",
"affected_version":{
"operator":"",
"raw_version":"3.0pl1-128+deb9u1",
"version":"3.0pl1-128+deb9u1",
"major":null,
"minor":null,
"patch":null
},
"fixed_version":null,
"title":"vixie-cron: memory consumption DoS via a large crontab file",
"description":"Vixie Cron before the 3.0pl1-133 Debian package allows local users to cause a denial of service (memory consumption) via a large crontab file because an unlimited number of lines is accepted.",
"severity":"Low",
"severity_source":"debian",
"references":[
"http://www.securityfocus.com/bid/107378",
"https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9705",
"https://lists.debian.org/debian-lts-announce/2019/03/msg00025.html",
"https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/6DU7HAUAQR4E4AEBPYLUV6FZ4PHKH6A2/",
"https://salsa.debian.org/debian/cron/commit/26814a26"
]
}
]
}
}
It's that simple to get started!
With the power of security scanning at your side, you've no reason not to keep on top of securing your packages!
More articles


Securing LLM dependencies against serialisation attacks

Top 10 most popular LLM models on Hugging Face

Protect your software supply chain from typosquatting with Cloudsmith

Securing AI-generated code with Cloudsmith

