OWASP CI/CD Part 9: Improper Artifact Integrity Validation
- OWASP CI/CD Part 1: Insufficient Flow Control
- OWASP CI/CD Part 2: Inadequate IAM
- OWASP CI/CD Part 3: Dependency Chain Abuse
- OWASP CI/CD Part 4: Poisoned Pipeline Execution (PPE)
- OWASP CI/CD Part 5: Insufficient PBAC
- OWASP CI/CD Part 6: Insufficient Credential Hygiene
- OWASP CI/CD Part 7: Insecure System Configuration
- OWASP CI/CD Part 8: Ungoverned Usage of 3rd Party Services
- OWASP CI/CD Part 9: Improper Artifact Integrity Validation
- OWASP CI/CD Part 10: Insufficient Logging and Visibility
Improper artifact integrity validation is a critical vulnerability in CI/CD pipelines characterised by insufficient mechanisms to cryptographically verify the authenticity and integrity of code and build artifacts traversing the pipeline. When these controls are weak or absent, adversaries with access to any pipeline stage can inject malicious or tampered artifacts that appear legitimate, enabling undetected propagation through the pipeline and eventual deployment into production environments.
Technical overview of the vulnerability
This issue originates from the failure to enforce strong cryptographic validation of artifacts and dependencies within the CI/CD workflow. Because modern pipelines frequently integrate internally developed code, third-party dependencies, container images, and Infrastructure-as-Code (IaC) manifests, multiple vectors exist where unverified or malicious components can infiltrate.
In particular, attackers exploiting weak artifact validation can:
- Insert malicious code in source commits, bypassing code signing controls.
- Replace build artifacts or dependencies in artifact repositories or mirrors.
- Modify cryptographic hashes or signatures to spoof legitimate artifacts.
- Exploit lack of multi-source verification to propagate tampered components.
Without strong end-to-end integrity checks, the CI/CD pipeline can end up acting as a trusted path for delivering compromised software.
Why Artifact Integrity Validation Matters
Artifact integrity validation guarantees that every software package, container image, and configuration file has not been altered from its original, verified state. This is achieved through cryptographic hashes (eg: SHA-256), digital signatures, and metadata attestations which provide strong guarantees of provenance and immutability.
By rigorously validating artifacts, development teams ensure:
- Protection against supply chain attacks involving compromised dependencies or build outputs.
- Detection of unauthorised modifications during artifact transit or storage.
- Preservation of pipeline trust boundaries, preventing malicious code from reaching production.
Failures in integrity validation have severe consequences, including covert insertion of backdoors, data exfiltration, service disruptions, and erosion of trust in automated deployment systems.
The Multi-Source Challenge in Modern Pipelines
The wide variety of inputs in CI/CD pipelines can introduce risk at every turn. For starters, code is often contributed by numerous developers spread across different teams and geographies, which means there's a constant stream of changes flowing into the system. These code commits can vary widely in quality and intent, making it critical to validate each one thoroughly. At the same time, build artifacts are produced incrementally at various stages of the pipeline. While this modular approach increases efficiency, it also opens up the possibility for inconsistencies or vulnerabilities to creep in if not carefully managed.
Another layer of complexity is added by the dynamic resolution of third-party dependencies and container images, which are frequently pulled in on the fly. These external components may not always be trustworthy or up-to-date, and can act as silent entry points for malicious code. Finally, the deployment process itself often relies on IaC templates, which are sometimes sourced from multiple repositories. This fragmented structure makes it harder to maintain visibility and control over what’s actually being deployed. Altogether, each of these inputs expands the pipeline's attack surface, further emphasising the need for rigorous validation and security checks at every step.
Core Components of Artifact Integrity Validation
Ensuring artifact integrity throughout the CI/CD pipeline is not a single-step task, you’ll need to implement a comprehensive, layered approach that addresses security at multiple levels. At the heart of this process are cryptographic checksums and digital signatures, such as SHA-256 hashes and GPG or X.509 signatures. These mechanisms verify that both source code commits and generated artifacts remain unaltered from their original, trusted state, providing a foundation of authenticity and non-repudiation. However, simply generating secure artifacts won’t solve all the issues. These artifacts must also be stored and distributed in a secure manner.
This is where secure artifact repositories come into play. These registries should be trusted, access-controlled, and designed to prevent tampering, ensuring that only authorised users and processes can interact with stored artifacts. Just as important is the secure transport of artifacts across pipeline stages. Enforcing end-to-end TLS encryption, along with mutual authentication between services, helps protect against interception or unauthorised modification during transmission. Underpinning all of this is the robust key management systems.
Signing keys must be protected using Hardware Security Modules (HSMs) or other secure vault solutions, with automated key rotation policies in place to reduce the risk of compromise over time. Together, these components form a cohesive security framework that protects artifacts from the moment they’re created, through every stage of the pipeline, all the way to final deployment.
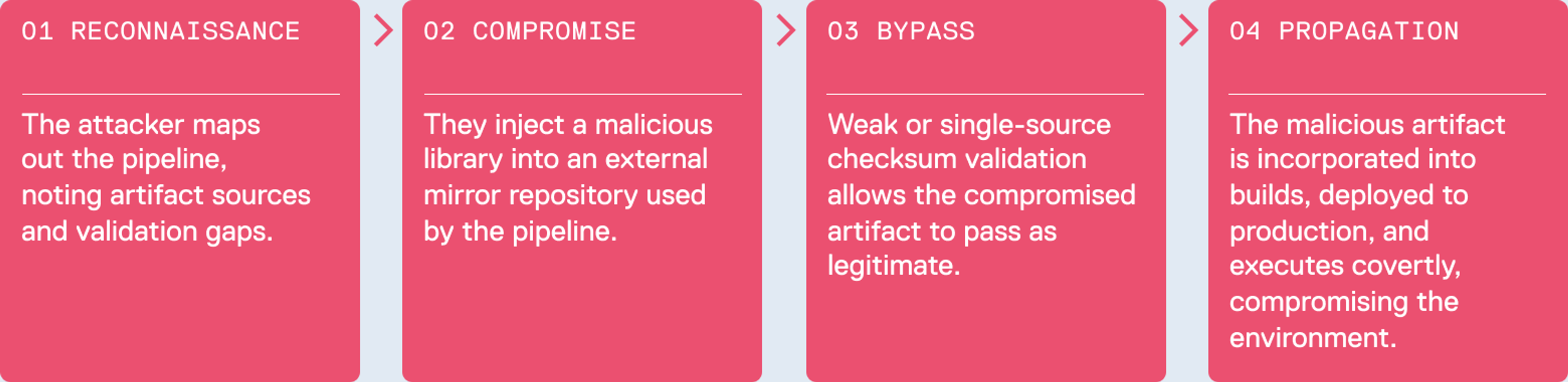
Hypothetical Tampered Artifact Injection Workflow
This type of attack re-emphasises the necessity for multi-layered validation and continuous monitoring in CI/CD pipelines.
How Cloudsmith Can Help Secure Artifact Integrity
Cloudsmith is a fully managed, cloud-native artifact repository built from the ground up with a focus on security and supply chain integrity. It offers a comprehensive set of capabilities designed to protect against risks like tampered, mis-validated, or malicious artifacts.
Immutable Storage & Versioning
Cloudsmith enforces immutability by ensuring that once an artifact is uploaded, it cannot be altered or deleted. This guarantees that the artifact remains in its original, trusted state. The attestation, along with the certificate, is recorded in Sigstore’s immutable transparency log, providing a permanent record of the artifact’s authenticity and provenance. Each artifact is versioned and linked to cryptographic hashes and rich metadata, providing a complete audit trail that can be used for traceability and forensic analysis in the event of an incident.
Cryptographic Signing and Verification
Cloudsmith supports automated signing of artifacts using tools like Sigstore’s Cosign for the actual artifact signing and in-toto for provenance, making it easier to embed trust into your software supply chain. These signatures can be verified before deployment or distribution, ensuring that only authorised and untampered artifacts are used in production environments.
Fine-Grained Access Control & Authentication
With robust user- and team-level RBAC and the ability to generate tightly scoped API tokens, Cloudsmith allows organisations to precisely define who can publish, read, or delete artifacts. This reduces the surface area for internal threats, and helps ensure that only trusted individuals can interact with critical software components.
Multi-Protocol Support with Secure Transport
Cloudsmith supports a wide array of package formats and protocols - including REST, OCI, Maven, npm, NuGet, Python (PyPI), and more. All transfers are encrypted with TLS, providing confidentiality and integrity during transit and reducing the risk of man-in-the-middle (MitM)-style attacks.
Integration with CI/CD Systems
Cloudsmith integrates seamlessly with popular CI/CD platforms like GitHub Actions, GitLab CI, CircleCI, Octopus Deploy, and so much more. These integrations allow teams to automatically publish signed artifacts and enforce policy checks (such as signature validation or provenance verification) at every stage of the delivery pipeline, embedding security directly into the development workflow.
Audit Logging and Monitoring
Cloudsmith offers comprehensive audit logs that provide a timeline view of non-package (but typically administrative) actions that have occurred within the repository, such as creating/modifying repository Retention Rules or creation of an Entitlement Token. These logs are essential for compliance and incident response, providing visibility into potential unauthorised usage patterns within the platform and development teams.
By using Cloudsmith as a central, security-aware artifact repository, your team can enforce strong cryptographic validation, limit exposure through precise access control, and maintain a clear audit trail. This makes it significantly harder for malicious or improperly validated artifacts to enter and propagate through the software supply chain.
Mitigation Best Practices Recap
To effectively defend against vulnerabilities stemming from inadequate artifact integrity validation, teams should adopt a series of interlocking best practices that reinforce trust across every stage of the software supply chain. A foundational step is implementing signed commits and enforcing commit signing policies within Source Code Management (SCM) systems. By requiring all commits to be signed with verified developer identities (and rejecting those that are not) businesses can ensure the authenticity of code contributions and trace their origins with confidence.
Beyond the source code itself, artifact signing and the use of in-toto attestations are critical for verifying the integrity and provenance of build outputs. With the right tooling, teams can sign every artifact generated during the build process and produce cryptographically verifiable attestations that describe how, when, and with what inputs those artifacts were created. This establishes a transparent, tamper-evident trail from source to binary.
Third-party components are another common source of risk. To mitigate this, it’s essential to perform multi-source integrity checks on all external dependencies. This means verifying package or container digests against official vendor-provided checksums and cross-referencing those results with additional trusted sources, reducing the chance of accepting a compromised or spoofed dependency.
Equally important is the secure storage of build artifacts. Repositories such as Cloudsmith provide access controls, audit logging, and built-in protections against unwarranted changes, helping to ensure that only validated artifacts make it into later stages of the pipeline or into production environments.
Finally, security shouldn't end once an artifact is deployed. Continuous drift detection and monitoring are crucial for identifying anomalous changes to IaC configurations or runtime environments. Free open-source tools such as Sysdig’s Falco can help detect early signs of Github account modifications, allowing teams to respond quickly and maintain a strong security posture over time.
Together, these practices create a resilient defence against integrity-based attacks, reducing the risk of compromised artifacts reaching production systems.
The Road Ahead
Improper artifact integrity validation remains a critical attack vector threatening software supply chain security. By adopting comprehensive cryptographic validation, secure artifact storage, and vigilant monitoring (all achievable within Cloudsmith) you can significantly reduce the risk of malicious code propagating unnoticed into production environments.
In the next and final instalment of this series, we will examine the last major risk identified in the OWASP Top 10 for CI/CD systems, which deals explicitly with insufficient logging and visibility. Reading through this series, and the associated OWASP eBook, readers should be provided with a consolidated framework for securing their entire software delivery lifecycle end-to-end. Stay tuned.

More articles

OWASP CI/CD Part 2: Inadequate IAM
OWASP CI/CD Part 3: Dependency Chain Abuse
OWASP CI/CD Part 4: Poisoned Pipeline Execution (PPE)
OWASP CI/CD Part 5: Insufficient PBAC
OWASP CI/CD Part 6: Insufficient Credential Hygiene
OWASP CI/CD Part 7: Insecure System Configuration
OWASP CI/CD Part 8: Ungoverned Usage of 3rd Party Services
OWASP CI/CD Part 9: Improper Artifact Integrity Validation