
Mastering Open Source Security: Your Guide to S2C2F

Welcome to our 2nd blog in our series on how to securely consume Open Source Software (OSS).
Attacks targeting OSS are on the rise, making the security of your software supply chain a top priority. The 1st blog gave an overview of some of the most common types of attacks. Today we’ll explore the Secure Supply Chain Consumption Framework (S2C2F) that can help you mitigate against these attacks.
About S2C2F
In 2019, Microsoft launched an internal initiative to secure its own development practices around the consumption and management of OSS. They donated the resulting framework, originally called the Open Source Software-Secure Supply Chain (OSS-SSC) framework, in 2022 to the Open Source Security Foundation (OpenSSF). Renamed S2C2F, the framework now has its own Special Initiative Group (SIG) underneath the Supply Chain Integrity Working Group.
S2C2F consists of eight core principles and four maturity levels, providing a comprehensive strategy for organizations to incrementally improve their security posture when consuming OSS.
The framework is not revolutionary: it's a practical guide to knowing what OSS you are using, preventing the consumption of vulnerable packages, and efficient patch management.
Cloudsmith and S2C2F
By using Cloudsmith, you can get a big head start on implementing S2C2F principles, and improving your team’s S2C2F maturity level. Specifically, you can use Cloudsmith to -
- Centralize your OSS asset store
- Proxy and cache OSS dependencies
- Implement robust policy management
- Ensure comprehensive package and container scanning
- Create rules for vulnerability mitigation
- Automate workflows for a wide variety of package formats, CI/CD integrations, CLI, APIs, and webhooks
TLDR
In this article, we will explore the fundamental principles and ascending maturity levels of the Framework, providing examples of real-world threats it can effectively counter. Additionally, we will illustrate how Cloudsmith assists in implementing these principles, helping you achieve your desired level of maturity.
S2C2F Principles
The framework consists of the following 8 principles. By implementing practices for each, you can create a robust and secure supply chain:
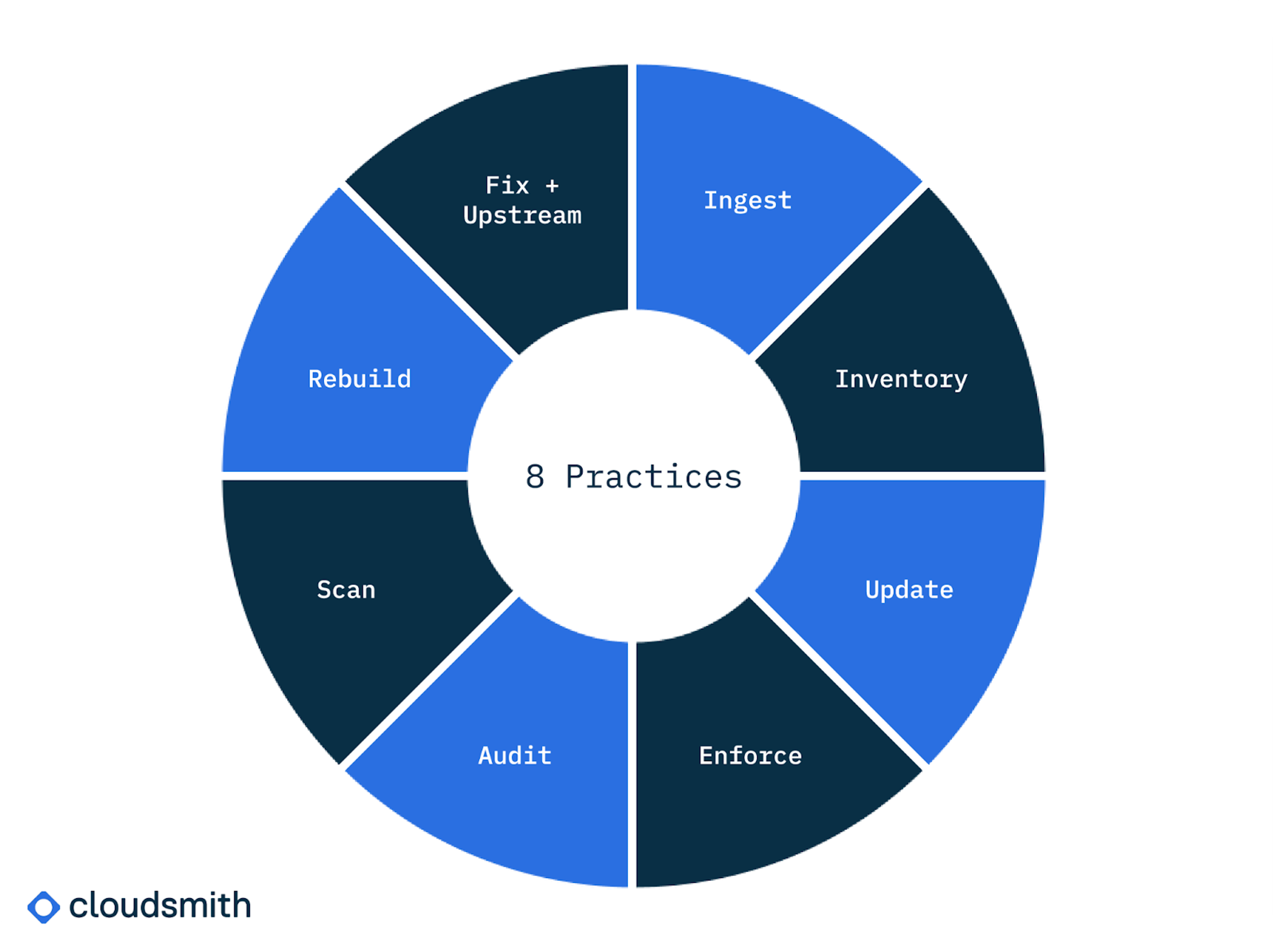
- Ingest - Consume your OSS from 1 location controlled by your organization, like Cloudsmith.
- Inventory - Create a list of all your OSS dependencies.
- Update - Update known vulnerabilities in a timely manner.
- Enforce - Force developers to adopt secure practices.
- Audit - Audit that developers are consuming through the approved ingest method, Validate the integrity of the OSS that you are consuming.
- Scan - Scan for malware and vulnerabilities using automation where possible.
- Rebuild - Rebuild OSS on Trusted Infrastructure.
- Fix Upstream - Have the ability to fork and fix code when necessary for a temporary fix.
S2C2F Maturity Levels
The Framework applies these 8 principles across 4 maturity levels to enhance open-source security. Levels 1 and 2 provide the basics for a solid OSS governance program. Levels 3 and 4 get into proactive measures and more sophisticated types of controls.
Let’s have a look at the 4 maturity levels in more detail.
Level 1- focus on Ingestion
How you ingest your OSS is the most important thing to focus on when getting started with implementing this framework, says Adrian Diglio, Principal PM Manager of Secure Software Supply Chain (S3C), Microsoft at his RSA 2023 talk Introducing the Secure Supply Chain Consumption Framework.
S2C2F strongly advocates the adoption of an artifact repository like Cloudsmith as a central location for all OSS packages. It's a single point to initiate policy enforcement, conduct scans, and implement stringent security controls for your OSS.
This approach guarantees the availability of OSS package dependencies and acts as a safeguard against potential upstream disruptions like the infamous NPM left-pad incident, where a package Maintainer withdrew a popular package from its public repository.
Level 1 requirements:
- Use package managers
- Local copy of the artifact
- Scan with known vulnerabilities
- Scan for software licenses
- Inventory OSS, hopefully in a standard format like Software Bill Of Materials (SBOM)
- Manual OSS updates
Level 2: Secure Consumption and Improved MTTR
Level 2 requires organizations to focus on identifying known vulnerabilities in the OSS they use. This includes using Software Composition Analysis (SCA) tools to scan and detect security issues and automatically update OSS.
Level 2 requirements:
- Scan for whether the OSS are end-of-life
- Have an incident response plan
- Automatic OSS updates
- Alert on vulnerabilities at PR time
- Audit that consumption is through the approved ingestion method
- Validate integrity of OSS
- Secure package source file configuration
Level 3: Malware Defense and Zero Day Detection
In Level 3, the emphasis turns to mirroring external OSS internally. This safeguards organizations with local, controlled package copies, reducing vulnerabilities like the previously mentioned left-pad incident. It also encourages proactive security, including fuzzing, static analysis, and other methods to uncover potential code vulnerabilities.
Level 3 requirements:
- Deny list capability
- Clone OSS source
- Scan for malware
- Proactive security reviews for yet to be discovered vulnerabilities
- Enforce OSS provenance
- Enforce consumption from curated feed
- Verifying the provenance of all open source components to make the binaries match the purported source code
Level 4: Advanced Threat Defense
This level is considered aspirational in most cases as it is difficult to implement at scale. It involves rebuilding OSS on Trusted Infrastructure. Also in extreme cases, when a critical vulnerability is discovered, organizations may implement private fixes as a temporary risk reduction measure. This would involve forking the code, implementing the fix and then releasing this version on a temporary basis with the intent of pushing this fix to the main branch as soon as possible.
Level 4 requirements:
- Validate the SBOMs of OSS consumed
- Rebuild OSS on trusted infrastructure
- Digitally sign rebuilt OSS
- Generate SBOM for rebuilt OSS
- Digitally sign protected SBOMs
- Implement fixes
Elevate Your S2C2F Game with Cloudsmith
Cloudsmith is your trusted ally, propelling your S2C2F implementation. Our platform is equipped with a suite of features that align seamlessly with S2C2F principles:
Ingest: Cloudsmith isolates and protects your software supply chain from public upstream sources like Maven Central by proxying or caching your OSS artifacts. This protects you from outages or left-pad incidents where an OSS package is removed unexpectedly from an upstream.
Inventory: Discover and track your dependencies, even their dependencies, using Cloudsmith. Store and validate SBOMs with ease.
Update. Benefit from our powerful integrations with CI/CD tools and APIs, enabling effortless automatic updates.
Scan. Cloudsmith automatically scans all packages for malware upon upload and provides vulnerability scanning for CVEs. Our APIs and webhooks facilitate seamless CICD integrations, empowering you to harness security tools beyond Cloudsmith.
Enforce: Take command with Cloudsmith's policy management features. Centralize rules for software artifacts, manage licenses, vulnerabilities, quarantining and our soon to be released deny lists feature. Easily set your repository to only accept immutable artifacts, semantic versioning or a certain vulnerability level.
Audit: Find out where your packages came from with Cloudsmith. Sign, verify, and trust your OSS sources using metadata, sigstore, checksums, and dependency insights. Streamline package discovery, ensure license compliance, and enhance provenance.
Rebuild: Cloudsmith's support for signing and SBOMs help you verify the provenance of your build.
Fix Upstream: Host, tag and sign your packages for temporary builds that fix vulnerabilities.
Cloudsmith, coupled with tooling for updating dependencies, getting information about maintainers, and creating SBOMs, can get you to your desired S2C2F level.
Matching levels to real-world attacks
Data from the Secure Supply Chain Consumption Framework (S2C2F) SIG, provides illustrative instances of real-world attacks that the S2C2F framework could have effectively countered.
Conclusion
The S2C2F is a pragmatic approach to securing how you consume OSS. It emphasizes the fundamental principles of knowing your OSS, preventing the introduction of vulnerable packages, and maintaining robust patch management. We at Cloudsmith are big believers in S2C2F!
Keep an eye out for our next blog, where we'll give you actionable steps to implement S2C2F with the help of Cloudsmith.
If you want to discover more about how Cloudsmith can help you secure your supply chain, sign up for a free trial or open a chat from our website.
More articles


Securing LLM dependencies against serialisation attacks

Top 10 most popular LLM models on Hugging Face

Protect your software supply chain from typosquatting with Cloudsmith

Securing AI-generated code with Cloudsmith

