
Cloudsmith's Enhanced Security with Policy Management

Software development and distribution are becoming increasingly complex, and potential vulnerabilities and threats are multiplying by the dozen. This makes the need for robust security measures even more critical - everything you’ve built could be at risk. Recognizing this, Cloudsmith has always been at the forefront of ensuring that software artifacts are managed efficiently and securely. As a part of this continuous effort, we have recently released a suite of Policy Management features to help streamline security operations, ensuring efficient governance of software artifacts that are actively fortified against lurking threats.
Policy Management: Centralized Oversight and Control
Policy management is a crucial component that ensures a secure, compliant, and efficient software environment. At its core, policy management provides a centralized system to define, implement, and enforce rules and protocols related to software artifacts. This centralized approach ensures that there's a consistent application of security measures across the board, reducing the chances of vulnerabilities slipping through the cracks.
Cloudsmith's policy management system is designed with the user in mind, with the following pillars at the forefront:
Ease of use: With an intuitive interface, Cloudsmith ensures that setting up and managing policies is straightforward, even for those who might not be deeply technical. This user-friendly approach ensures that teams can quickly implement and adapt policies without a steep learning curve.
- Flexibility: Recognizing that no two software environments are the same, Cloudsmith's policy management system is built to be flexible. Users can customize policies to fit their specific needs, ensuring that the security measures are tailored to their unique environment.
- Comprehensive coverage: Cloudsmith's policy management doesn't just focus on one aspect of security - it provides a holistic approach, covering everything from package signing and access controls to vulnerability scanning. This comprehensive coverage ensures that all potential security threats are addressed.
- Compliance enforcement: Once policies are set, Cloudsmith ensures they're consistently enforced. The system automatically checks for compliance, ensuring that any deviations are quickly identified and addressed.
Authentication Policies: Fortifying Access Control
Authentication policies are predefined sets of rules that determine who can access what. They are the backbone of a secure software environment, ensuring that unauthorized users are kept at bay.
Cloudsmith's recent enhancements in this domain are a testament to its commitment to robust security. The newly introduced authentication policies now allow organizations to enforce API-Key rotation at an organizational level. While users previously had the option to manually rotate their keys, the game has changed.

Organizations can now set specific time periods for key refreshes or outright block keys that haven't been updated within the stipulated timeframe. This proactive approach ensures that stale or potentially compromised keys don't linger, thereby bolstering the platform's security.
Drawing lessons from the CircleCI breach on January 4, 2023, Cloudsmith advocates for a series of measures to enhance pipeline security. In response to the breach, Cloudsmith has added support for OIDC tokens. These tokens are a more secure alternative to long-lived credentials, reducing the risk of unauthorized access. By using OIDC tokens, users can avoid storing these credentials in CircleCI, further safeguarding their operations.
License Policies: Ensuring Compliance and Governance
Software licensing dictates how software can be used, modified, and distributed. While these licenses offer a framework for software utilization, they can also come with certain restrictions or obligations. For instance, some licenses may impose clauses that restrict the use of the software or mandate the sharing of modifications made to the software. Ensuring compliance with these licenses is not just a matter of ethical software use, but also a legal necessity.
Cloudsmith's license policies are designed to simplify complexity. With the ability to flag or quarantine packages that fall under an organization's "do not use" category, Cloudsmith ensures that you're always in compliance with licensing requirements. This is especially crucial for licenses that have restrictive clauses or necessitate sharing modifications. By automating these license checks, Cloudsmith saves you time and significantly reduces the risks associated with non-compliance.
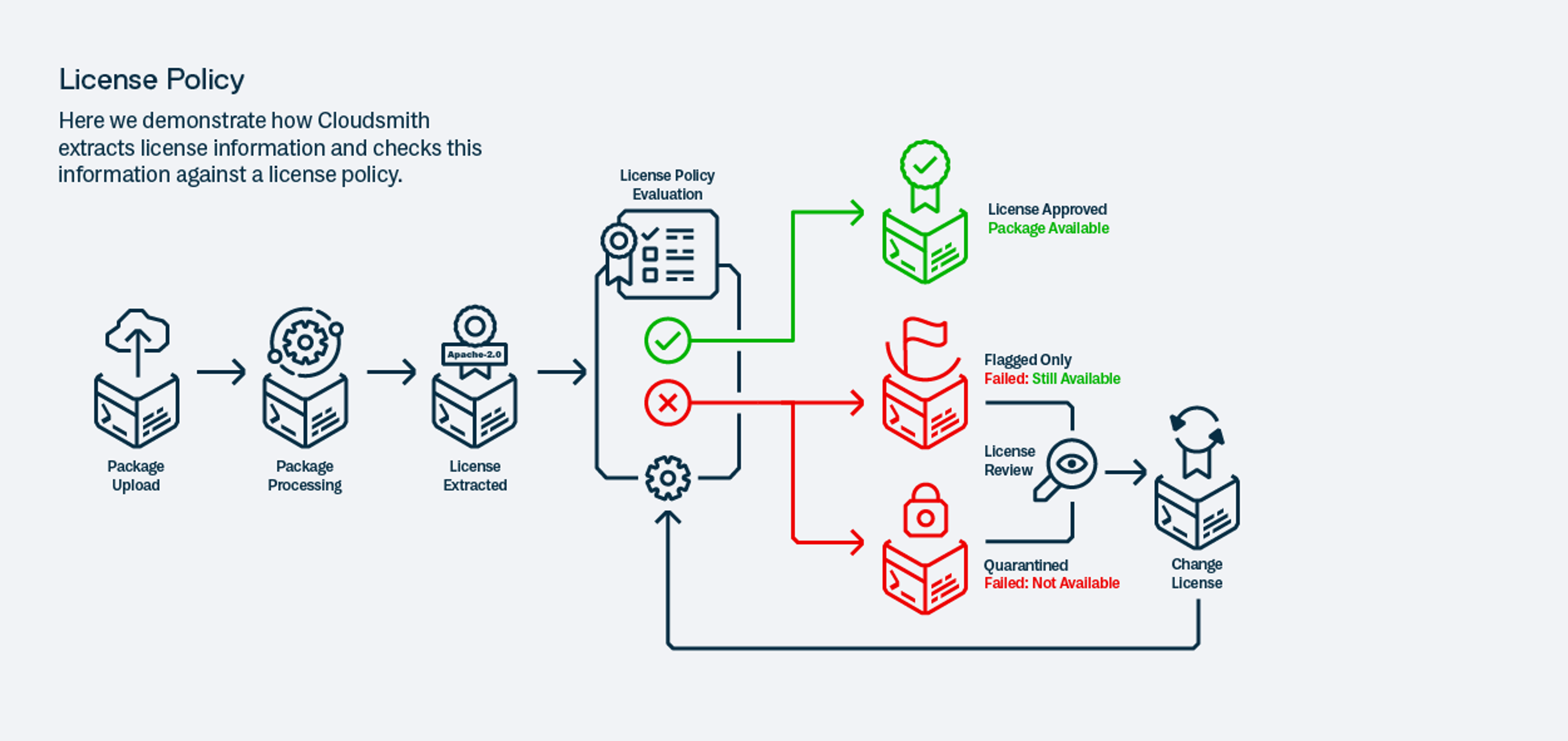
A real-world example of the importance of license compliance can be seen in the recent challenges faced by farm equipment maker, John Deere. The Software Freedom Conservancy (SFC) highlighted John Deere's non-compliance with the General Public License (GPL). The GPL requires users of such software to share source code, ensuring a level of transparency and collaboration. The SFC's contention was that John Deere, by not living up to these licensing commitments, was jeopardizing farmers' ability to repair their tools, impacting their livelihood.
John Deere's non-compliance with GPL is a stark reminder of the potential legal and ethical pitfalls of not adhering to software licenses. The company faced multiple lawsuits from farmers and even drew attention from the Justice Department and the White House. While John Deere did eventually strike a deal to provide farmers with greater access to their equipment's internal workings, the situation underscores the importance of license compliance.
Cloudsmith's license policies aim to prevent such scenarios. By ensuring that organizations are always in line with their software licensing commitments, Cloudsmith helps in creating an environment of trust, transparency, and legal compliance.
Vulnerability Policies: Proactive Threat Mitigation
The emphasis on continuous integration and deployment has brought about a parallel need for continuous security. Vulnerability management, once a periodic audit activity, has now become a daily concern. This makes it imperative for teams to have tools that can detect and address vulnerabilities as early as possible in the software lifecycle.
Cloudsmith’s policies are designed to be both comprehensive and customizable, ensuring that teams can maintain a robust security posture without compromising on agility.
One of the standout features of Cloudsmith's vulnerability policies is the automatic scanning of artifacts for Common Vulnerabilities and Exposures (CVEs) upon upload. The real power of these policies lies in the automated actions they can trigger. Depending on the detected vulnerabilities and their severity, Cloudsmith can either flag them for review or quarantine the affected artifacts, effectively blocking downloads. This level of automation ensures that potential threats are addressed even before they can make their way into production environments. For instance, a team might choose to get notified for low or medium severity vulnerabilities but block artifacts with high or critical vulnerabilities outright.
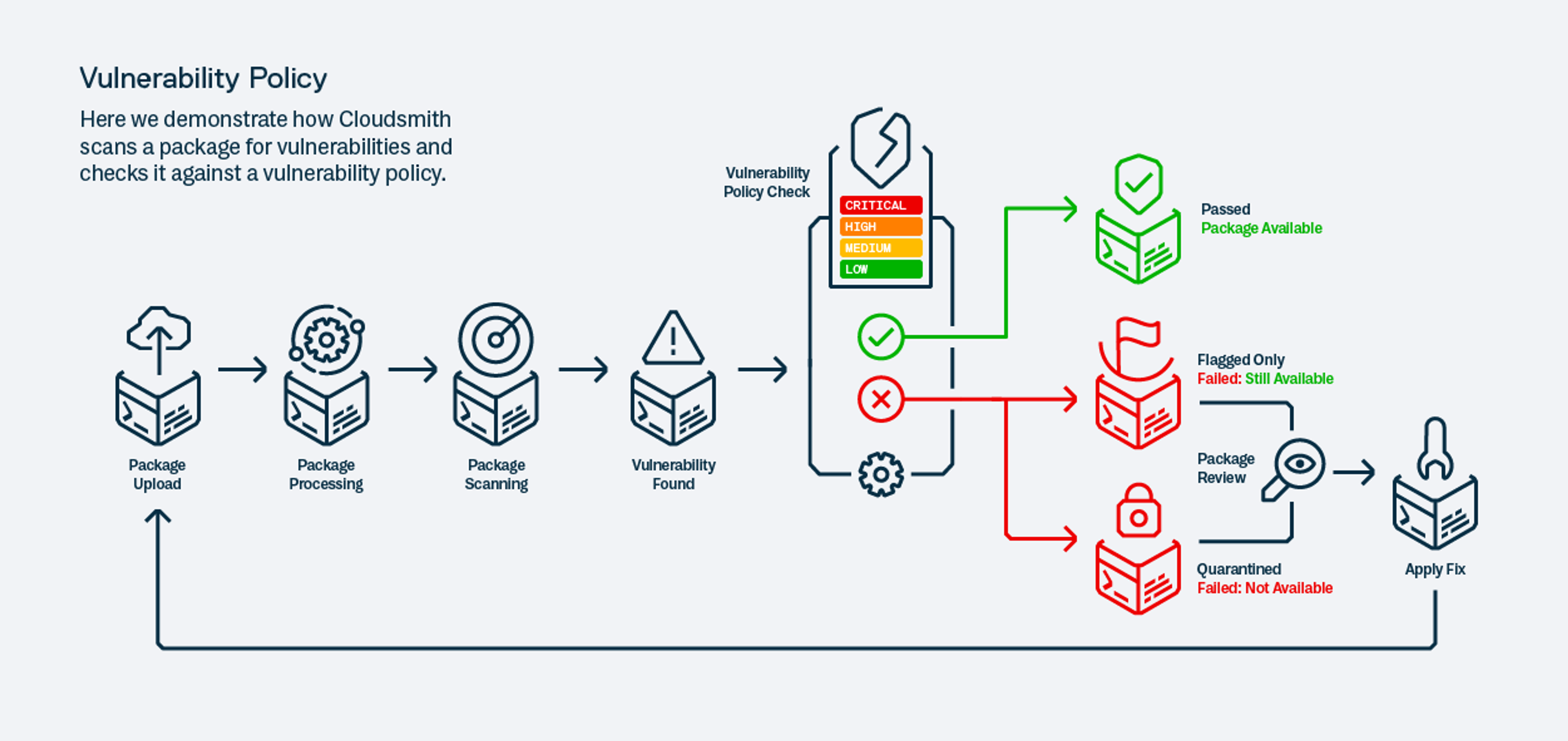
Cloudsmith's vulnerability policies are not a one-size-fits-all solution. They offer granular controls, allowing teams to specify actions based on package names, versions, or version groups. This ensures that the policies are in line with the specific risk appetites and operational nuances of different projects or teams.
But what about vulnerabilities discovered after the initial upload? Cloudsmith has that covered too. Teams can trigger additional scans post-upload, ensuring that their artifacts are continuously evaluated against the latest threat intelligence. This continuous evaluation ensures that even if a vulnerability is discovered after the initial scan, it can be promptly addressed, keeping the software environment secure and compliant.
As software threats evolve as fast as the software itself, Cloudsmith's vulnerability policies offer teams the tools they need to stay a step ahead, ensuring that security is constantly proactive.
The Bigger Picture: Cloudsmith's Holistic Approach to Security
Cloudsmith's security strategy is about anticipating future challenges, adapting to technology’s changing landscape, and ensuring that the platform remains several steps ahead of potential risks. Our newly introduced features, including Policy Management, are a testament to this forward-thinking approach - they are designed to lay the groundwork for a safer, more secure future in software distribution.
Teams that build and deploy mission-critical software need sophisticated controls. These software teams look for fine-grained user management policies, role-based access controls, and enterprise-class enforcement and reporting. Cloudsmith was built with these teams in mind.

More articles


Cloudsmith 2025: By the Numbers

Extending supply chain governance to AI and ML artifacts

The Artifact Management Market Is Up For Grabs
Prototyping an MCP Server

