
Secure Open Source Consumption: Level 1 of S2C2F

Attacks targeting open source software (OSS) are on the rise, making the security of your software supply chain a top priority. What do you have to do, exactly, to secure your software supply chain?
This is the third blog in a Cloudsmith series about software supply chain security. The first blog gave an overview of the most common types of attacks on OSS. Next, we explored the Secure Supply Chain Consumption Framework (S2C2F), which is designed to mitigate against these attacks.
Level 1 of S2C2F is the bare minimum organizations should do to securely consume OSS. Today's blog focuses on the actionable steps and essential tools required to attain Level 1.
Level 1 primarily centers on the ingestion of OSS and requires the following:
- Use an artifact repository (like Cloudsmith!) to cache OSS
- Maintain an automated OSS inventory, such as a software bill of materials (SBOM)
- Scan OSS for known vulnerabilities and licenses
- Update your vulnerabilities (manually is okay at this level)
A major step in Level 1 is the adoption of an artifact repository like Cloudsmith as a central location for all OSS packages. This facilitates applying security controls for your OSS, and guarantees the availability of OSS package dependencies and protects you from incidents like the npm left-pad vulnerability.
S2C2F
Let's refresh on the eight principles of S2C2F:
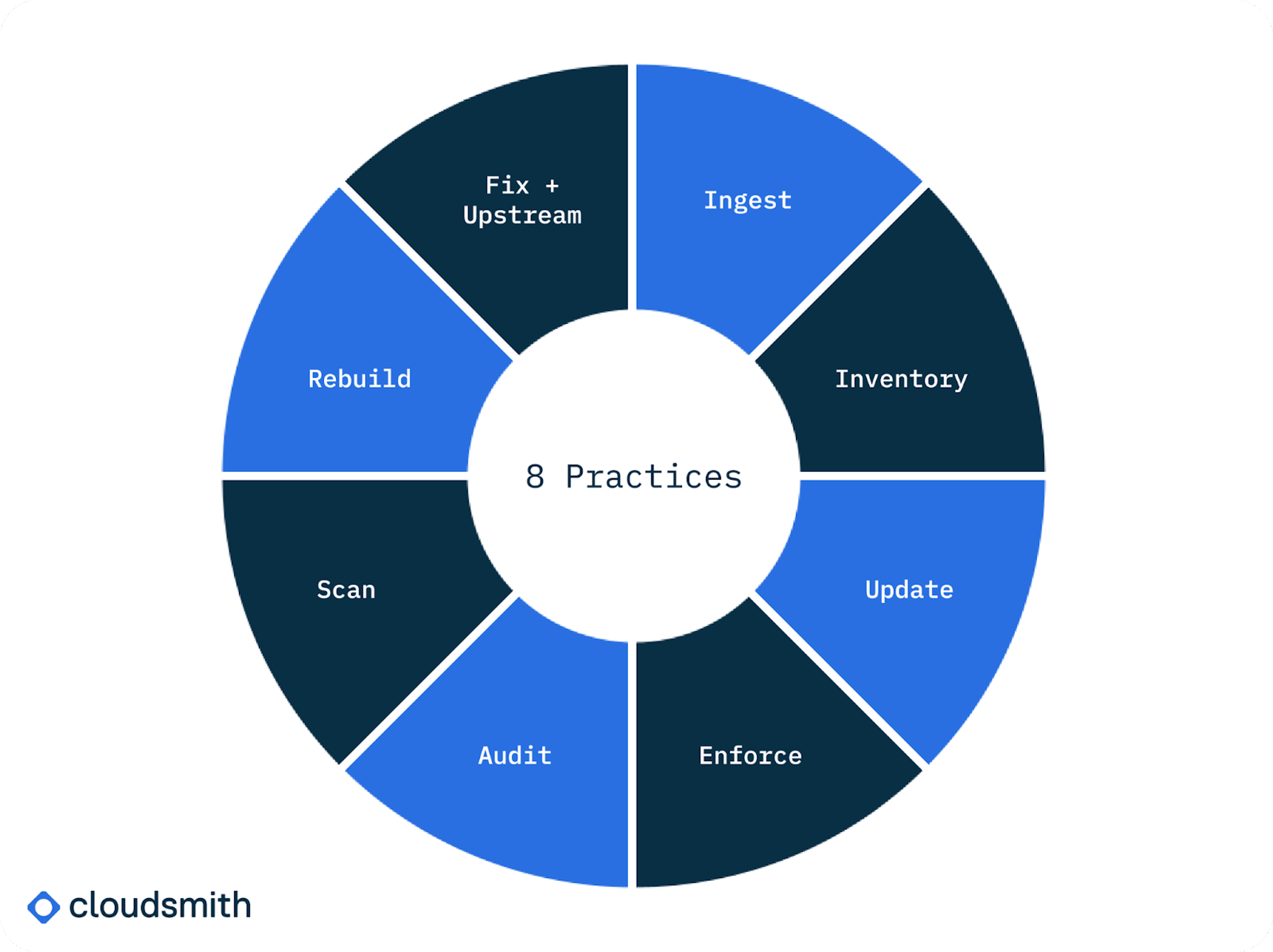
- Ingest — Consume your OSS from one location controlled by your organization, like Cloudsmith.
- Inventory — Create a list of all your OSS dependencies.
- Update — Update known vulnerabilities in a timely manner.
- Enforce — Force developers to adopt secure practices.
- Audit — Audit that developers are consuming through the approved ingest method, and validate the integrity of the OSS that you are consuming.
- Scan — Scan for malware and vulnerabilities using automation where possible.
- Rebuild — Rebuild OSS on trusted infrastructure.
- Fix Upstream — Have the ability to fork and fix code, when necessary, for a temporary fix.
Steps to Level 1
Level 1 of the S2C2F concentrates on the Ingestion, Inventory, Scan and Update principles. The following initiatives are required:
Pre-assessment
Before you start implementing changes in your organization to align with S2C2F it is advised that you perform an assessment of the organization's degree of maturity in software developer OSS management, security, and consumption processes.
Ingest it
Package manager
Use a package manager to consume OSS packages. A package manager keeps track of what software is installed on your computer, and allows you to easily install new software, upgrade software to newer versions, or remove software that you previously installed. Scroll to the table below for a list of commonly used languages and their respective package format, registry, etc.
Artifact repository
Use an artifact repository like Cloudsmith to host all of your software packages and OSS packages. To set up Cloudsmith to cache your upstream OSS, do the following:
- Update your software’s configuration file to point to your artifact repository (see the table below for the settings file for popular languages).
- Start hosting your OSS packages on Cloudsmith by caching your public repositories or upstreams. If the upstream repository you depend on goes down or is otherwise unavailable, your team can still access your cached versions stored in Cloudsmith. Cloudsmith will scan all the OSS packages for malware and vulnerabilities and also extract their licenses. This setup empowers our users to apply customized policies for enhanced security and management.
Inventory it
Automated OSS inventory
Level 1 of S2C2F requires organizations to maintain an automated inventory of all OSS used in development. There are a number of ways to take an inventory of your OSS
- The gold standard for inventorying your OSS is to generate a Software Bill of Materials (SBOM) at build time. An SBOM is an ingredient list of all the dependencies in your software in a standardized format. SBOMs are needed for more advanced levels of this framework. OSS tools to generate SBOMs that can be integrated into your CI/CD include Dependency-Track, cyclone dx tooling, syft and trivy.
- If you cache and proxy all the public registries that your organization uses on Cloudsmith, you can search for all packages that originated from an upstream via the UI or API by searching for tag:upstream (or even tag:maven-central if that's what you named the upstream when setting it up etc).
- You can use your software’s dependency file (e.g. requirements.txt for Python builds) to see what dependencies your software is pulling in. This file may not include your software’s transitive dependencies (your dependencies’ dependencies).
Scan it
Scan for known vulnerabilities
Scan OSS for known vulnerabilities (i.e. CVEs, GitHub Advisories, etc.). Here are a few ways to do this:
- Ideally you are integrating scanning tools early in your software development process using free tools like grype or paid tools like snyk.
- Cloudsmith scans cached OSS for malware and vulnerabilities. You can set a policy so that all packages must be above a certain vulnerability level and you can rescan a package for vulnerabilities.
Scan for OSS licenses
Scan all the OSS in your organization for licenses.
- Cloudsmith will extract the license for all cached OSS packages. Cloudsmith’s license policies allow you to define which package licenses are allowed within your organization.
- Alternatively you can use OSS ScanCode to detect OSS licenses.
Update it
Update Manually
Update vulnerable OSS manually using the results of your scanners, Level 1 S2C2F requires you to update vulnerable OSS manually. The framework advises that every organization should aspire to patch vulnerable OSS packages in under 72 hours. More advanced levels of S2C2F require you to use tools like Dependabot to help you automate this process.
Conclusions
By prioritizing ingestion, inventory management, and scanning, you'll bolster your software supply chain's resilience against potential threats. Leveraging package managers, artifact repositories like Cloudsmith, and automated inventory tools enhances security and guarantees availability when consuming OSS.
What’s next from Cloudsmith? In future blogs, we’ll discuss how you can achieve the advanced S2C2F framework levels, offering actionable steps to further enhance your OSS consumption practices and fortify your software ecosystem.
More articles


Securing LLM dependencies against serialisation attacks

Top 10 most popular LLM models on Hugging Face

Protect your software supply chain from typosquatting with Cloudsmith

Securing AI-generated code with Cloudsmith

